Canon PowerShot SX730 HS review
-
-
Written by Ken McMahon
Quality
To test real-life performance, I shot this scene with the Canon PowerShot SX730 HS and Panasonic Lumix TZ90 / ZS70 using their best quality JPEG settings and at their base 80 ISO sensitivity setting. Both cameras were mounted on a tripod and image stabilisation was disabled, the sensitivity was manually set to 80 ISO and Aperture priority mode was selected for the exposure. I set the Aperture to f3.3 which I’d previously determined produced best results and both cameras selected a shutter speed of 1/1250.

As usual, the crops below are taken from the areas marked in red above. For this test both cameras were set to their maximum wide angle setting of 24mm, scroll down the page to see more results with the lenses zoomed in.
Both the PowerShot SX730 HS and Lumix TZ90 / ZS70 have a 20 Megapixel sensor that produces 4:3 proportioned images 5184×3888 pixels in size, so these crops are identical in terms of the area and the size of the detail.
The PowerShot SX730 HS gets off to an excellent start. Usually you’d expect to see some softness and distortion at the edge of the frame but this crop is pretty sharp and distortion free. There are lots of crisp edges – the window frame for example and there’s plenty of detail in those roof tiles. I can make out the tiniest hint of colour fringing around the window frame and it also looks a little bit noisy there, but I’m being really picky, this is about as good as it gets in this class of camera.
If it’s good at the edge, you’d expect the SX730 HS to provide even better quality in the middle of the frame and it doesn’t disappoint. Lots of fine detail and nice sharp edges, so nothing to complain about here. In the final crop from the right frame edge that chromatic aberration is a little more obvious and this crop looks a little softer and less detailed than the one from the opposite side. But overall this is a really excellent result from The PowerShot SX730 HS at the 24mm wide angle focal length.
Overall, the crops from the Lumix TZ90 / ZS70 at this focal length are softer, noisier and lack the detail that’s visible in the SX730 HS crops. The difference is most striking in the first crop. The Lumix TZ90 / ZS70 on the right is quite soft and lacking in detail, plus there’s a little bit of colour fringing around the window frame (it would probably be more visible if it weren’t for the softness). There’s also some evidence of noise in this first crop, with shadow detail looking a little clumpy.
The margin of difference narrows with the next two crops from the middle of the frame. There’s now a little more detail in the Lumix TZ90 / ZS70 crops, but the noise is still taking the sharpness off the edges. And the final pair of crops from the right frame edge, the PowerShot SX730 HS is again sharper and more detailed than the Lumix TZ90 / ZS70. Scroll down to see how these two models compare when zoomed in to around 150mm.

Above left: Canon PowerShot SX730 HS at 4.3mm (24mm equivalent) f3.3 80 ISO.
Above right: Panasonic Lumix TZ90 / ZS70 at 4.3mm (24mm equivalent) f3.3, 80 ISO.

Above left: Canon PowerShot SX730 HS at 4.3mm (24mm equivalent) f3.3 80 ISO.
Above right: Panasonic Lumix TZ90 / ZS70 at 4.3mm (24mm equivalent) f3.3, 80 ISO.

Above left: Canon PowerShot SX730 HS at 4.3mm (24mm equivalent) f3.3 80 ISO.
Above right: Panasonic Lumix TZ90 / ZS70 at 4.3mm (24mm equivalent) f3.3, 80 ISO.

Above right: Above left: Canon PowerShot SX730 HS at 4.3mm (24mm equivalent) f3.3 80 ISO.
Panasonic Lumix TZ90 / ZS70 at 4.3mm (24mm equivalent) f3.3, 80 ISO.
Canon PowerShot SX730 HS quality at 151mm equivalent

Here I’ve zoomed both models in to an equivalent focal length of 151mm. As at the wide angle setting, the Canon PowerShot SX730 HS provides a sharp, detailed and distortion free crop from the left edge of the frame and things improve slightly as we move into the central area of the frame. Crop number three, which is from right in the middle of the frame is sharper than crop 2 from the top edge. The final crop from the right edge is the softest of the four, but all of them have a good level of detail with clean edges.
At this focal length the Lumix TZ90 / ZS70 ups its game considerably though, with a much more consistent set of results which overall I’d say just outdoes the Canon PowerShot SX730 HS. The first and second crops from the Lumix are just a little bit sharper than the Canon’s, on the third crop it’s too close to call and in crop 4 the Lumix has the edge again. That makes it 1-all. Scroll down for the decider at the Lumix TZ90 / ZS70’s maximum 720mm zoom.

Above left: Canon PowerShot SX730 HS at 27.1mm (151mm equivalent) f5.6 80 ISO.
Above right: Panasonic Lumix TZ90 / ZS70 at 27.1mm (151mm equivalent) f5.4, 80 ISO.

Above left: Canon PowerShot SX730 HS at 27.1mm (151mm equivalent) f5.6 80 ISO.
Above right: Panasonic Lumix TZ90 / ZS70 at 27.1mm (151mm equivalent) f5.4, 80 ISO.

Above left: Canon PowerShot SX730 HS at 27.1mm (151mm equivalent) f5.6 80 ISO
Above right: Panasonic Lumix TZ90 / ZS70 at 27.1mm (151mm equivalent) f5.4, 80 ISO.

Above left: Canon PowerShot SX730 HS at 27.1mm (151mm equivalent) f5.6 80 ISO.
Above right: Panasonic Lumix TZ90 / ZS70 at 27.1mm (151mm equivalent) f5.4, 80 ISO.
Canon PowerShot SX730 HS quality at 720mm equivalent

For this set of crops I zoomed the Lumix TZ90 / ZS70 to its maximum 720mm zoom position and zoomed the PowerShot SX730 HS in to match the field of view. Don’t forget the SX730 HS’s 40x zoom can go further than this – to an equivalent 960mm – you can see those results below these.
For the first time the PowerShot SX730 HS looks likes it’s struggling a little to maintain sharpness. The first crop is a little soft and those edges between the stones aren’t as sharp as they might be. The second crop from the top edge of the frame is a little sharper, but suffers a little from colour fringing and crop three from the middle of the frame lacks the sharpness that the SX730 HS’s lens can produce at wider focal lengths.
Conversely, this is the best of the three sets of crops produced by the TZ90 / ZS70 with good detail and sharp edges across the frame from edge-to-edge. The lens is performing much better at the maximum focal length than it did at either the 24mm wide angle or, to a lesser degree, zoomed in to 151mm. You can still make out the noise from the sensor – it’s most obvious in the shadows of the stonework in the second crop, but this is nonetheless a great performance from the Lumix TZ90 / ZS70.
By comparison, the PowerShot SX730 HS crops are good, but generally softer than those from the TZ90 / ZS70. They’re also prone to colour fringing, which is particularly visible in the second crop. This is pretty much a reversal of what we saw at the 24mm wide angle setting so, on balance, I think you’d have to call it a draw, with the PowerShot SX730 HS winning at the wide-angle setting, the Lumix TZ90 / ZS70 at its maximum 720mm zoom, and a similar level of performance in the middle.

Above left: Canon PowerShot SX730 HS at 131mm (731mm equivalent) f6.3 80 ISO.
Above right: Panasonic Lumix TZ90 / ZS70 at 129mm (720mm equivalent) f6.4, 80 ISO.
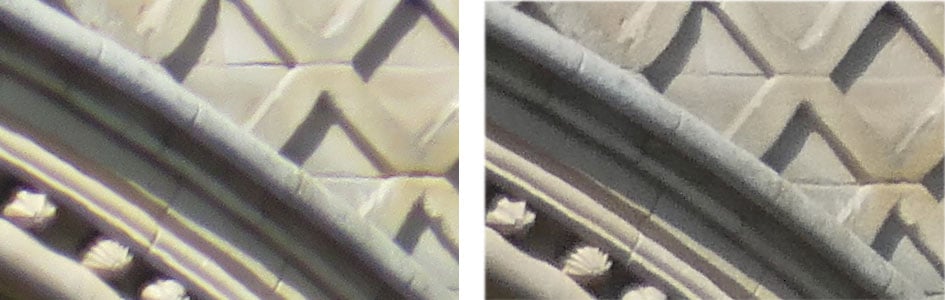
Above left: Canon PowerShot SX730 HS at 131mm (731mm equivalent) f6.3 80 ISO.
Above right: Panasonic Lumix TZ90 / ZS70 at 129mm (720mm equivalent) f6.4, 80 ISO.

Above left: Canon PowerShot SX730 HS at 131mm (731mm equivalent) f6.3 80 ISO.
Above right: Panasonic Lumix TZ90 / ZS70 at 129mm (720mm equivalent) f6.4, 80 ISO.

Above left: Canon PowerShot SX730 HS at 131mm (731mm equivalent) f6.3 80 ISO.
Above right: Panasonic Lumix TZ90 / ZS70 at 129mm (720mm equivalent) f6.4, 80 ISO.
Canon PowerShot SX730 HS quality at 960mm equivalent
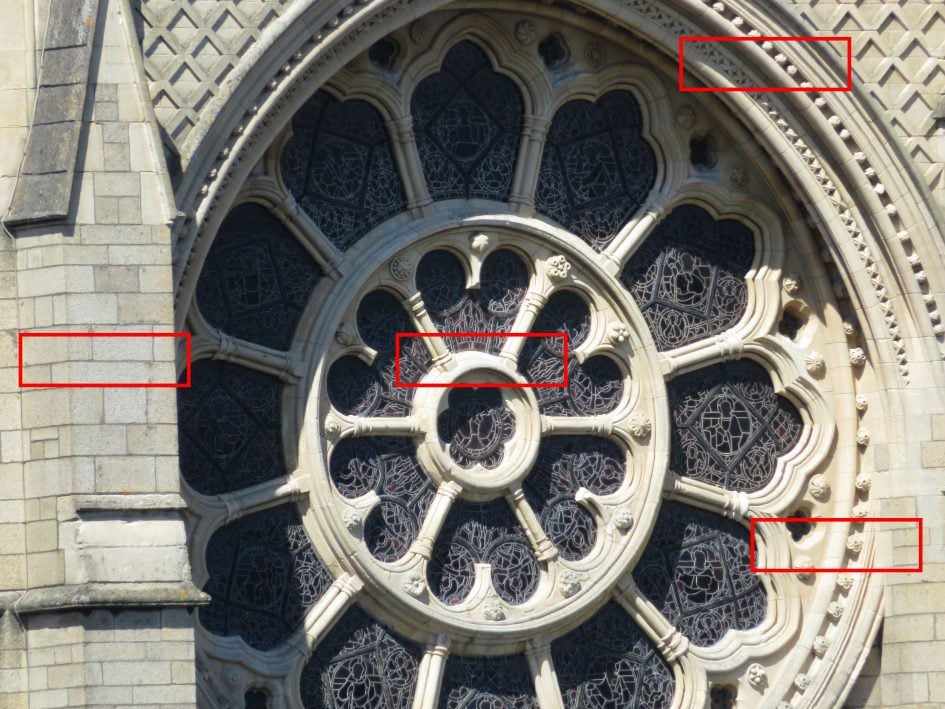
For this final set of crops I zoomed the PowerShot SX730 HS to it’s maximum 960mm equivalent focal length and took crops from the four areas marked in red above. There are no Lumix TZ90 / ZS70 crops for comparison here as the TZ90 / ZS70’s maximum zoom is reached at 720mm equivalent. If you haven’t already seen those results they’re just above.
These crops at 960m equivalent look pretty similar to those above at 720mm. If anything I’d say the edge crops look a tiny bit sharper by comparison, but there’s not a lot in it. One thing you can see more of is colour fringing, but it could just be it’s a little more visible in these bigger crops. One thing you can say is that there’s no drop in image quality going from 720mm to the SX730 HS’s maximum 960mm focal length.

Above: Canon PowerShot SX730 HS at 172mm (960mm equivalent) f6.9 80 ISO.

Above: Canon PowerShot SX730 HS at 172mm (960mm equivalent) f6.9 80 ISO.

Above: Canon PowerShot SX730 HS at 172mm (960mm equivalent) f6.9 80 ISO.

Above: Canon PowerShot SX730 HS at 172mm (960mm equivalent) f6.9 80 ISO.
Canon PowerShot SX730 HS JPEG Noise

To examine noise levels under real-life conditions, I shot this scene with the Canon PowerShot SX730 HS and the Panasonic Lumix TZ90 / ZS70 at each of their ISO sensitivities using their highest quality JPEG settings. Both cameras were mounted on a tripod and stabilisation was disabled.
The cameras were set to their maximum wide angle 24mm equivalent view. The ISO sensitivity was manually set to the lowest available setting and Aperture priority mode was selected for the exposure. I’d previously determined that best results were obtained at f3.3 so both cameras were set to f3.3 and at its base 80 ISO sensitivity setting the Lumix TZ90 / ZS70 selected a shutter speed of 1/5. I applied -1/3EV exposure compensation on the PowerShot SX730 HS to achieve a close to equivalent exposure of 1/6. As usual the crops below are taken from the area marked in red above.
The PowerShot SX730 HS, which like the Lumix TZ90 / ZS70 has a 20 Megapixel sensor, is a little noisy at its base 80 ISO sensitivity setting as you can see from the first crop on the left below. The same can be said of the Lumix TZ90 / ZS70 80 ISO crop opposite on the right, but the Canon’s noise is somehow less intrusive. It has a uniformly fine-grained appearance which is less disruptive of fine detail than the clumpy noise produced by the Lumix sensor.
Moving down to the 100 ISO crop, The SX730 HS is marginally noisier, but it’s actually quite hard to tell the difference looking at these 100 percent crops, so you’d be unlikely to notice ordinarily. At 200 ISO though there’s a much more noticeable step up in the noise. At each step up the sensitivity scale, the noise increases, pretty much linearly, I’d say you could expect to produce good quality 100 percent prints (about 25×20 inches) or view on a big screen without noticing the quality loss too much up to and including 400 ISO. Of course at smaller sizes – on a phone or tablet, or even a laptop – you’ve got more leeway and 800 or even 1600 ISO will look good. It’s at 1600 ISO though that things really begin to go South, with the noise gaining the upper hand over image detail.
3200 ISO is good to have for those ‘must have at any cost’ shots – the christenings in gloomy churches, or night shots where you don’t want to, or can’t use flash. I think Canon’s decision to call it a day at 3200 ISO is a sensible one, you only have to look at the 6400 ISO crop from the Lumix TZ90 / ZS70 to see that a compact sensor produces more noise than actual image data at such a high sensitivity setting.

Above left: Canon PowerShot SX730 HS at 80 ISO f3.3. Above right: Panasonic Lumix TZ90 / ZS70 at 80 ISO f3.3.

Above left: Canon PowerShot SX730 HS at 100 ISO f3.3. Above right: Panasonic Lumix TZ90 / ZS70 at 100 ISO f3.3.

Above left: Canon PowerShot SX730 HS at 200 ISO f3.3. Above right: Panasonic Lumix TZ90 / ZS70 at 200 ISO f3.3.

Above left: Canon PowerShot SX730 HS at 400 ISO f3.3. Above right: Panasonic Lumix TZ90 / ZS70 at 400 ISO f3.3.

Above left: Canon PowerShot SX730 HS at 800 ISO f3.3. Above right: Panasonic Lumix TZ90 / ZS70 at 800 ISO f3.3.

Above left: Canon PowerShot SX730 HS at 1600 ISO f3.3. Above right: Panasonic Lumix TZ90 / ZS70 at 1600 ISO f3.3.

Above left: Canon PowerShot SX730 HS at 3200 ISO f3.3. Above right: Panasonic Lumix TZ90 / ZS70 at 3200 ISO f3.3.

Above right: Panasonic Lumix TZ90 / ZS70 at 6400 ISO f3.3.
Next check out my sample images, my in-depth review or my final verdict.
Check prices on the Canon SX730 HS at Amazon, B&H, Adorama, or Wex. Alternatively get yourself a copy of my In Camera book or treat me to a coffee! Thanks!



