Olympus OM-D E-M1X review
-
-
Written by Gordon Laing
Intro
The Olympus OM-D E-M1X is a high-end mirrorless camera aimed at sports and wildlife professionals who demand speed and robustness. Announced in January 2019, it comes two years after the E-M1 Mark II and shares that model’s 20 Megapixel Four Thirds sensor, 4k video and fast burst shooting, but is larger and pitched at a higher level with an integrated battery grip, tougher credentials, improved autofocusing and even better stabilisation than before.
The E-M1X is the largest, heaviest and toughest camera in the Micro Four Thirds system to date, measuring 144x147x75mm and weighing 997g with its two battery packs fitted. With its integrated battery / portrait grip, it reminds you of the Canon EOS 1Dx Mark II or Nikon D5, but while the sensor is smaller, it’s accompanied by the broad and innovative Olympus feature-set. The E-M1X matches the resolution of the 1Dx II and D5, but offers faster 18fps burst shooting with autofocus, built-in image stabilisation good for up to a staggering 7.5 stops of compensation (with a Sync IS lens), built-in field receivers (tagging images with location, temperature, elevation and direction), 4k up to 30p in UHD or C4k formats, the ability to capture moments prior to fully-pushing the shutter release, a huge viewfinder magnification of 0.83x, a fully-articulated touchscreen, dual UHS II card slots, USB charging, and weather-sealing that exceeds IPX1. And while the E-M1X becomes the most expensive Micro Four Thirds camera to date at 2700 pounds, it remains roughly half the price of the 1Dx II and D5, not to mention a little smaller and up to a third lighter.
Other features include a 50 Megapixel composite High Res shot mode that now works handheld, 1080 video up to 120p, OM-Log400 for flat footage, anti-flicker capabilities, improved dust reduction and a shutter rated to 400k actuations.
Of course the 1Dx and D5 both sport much larger full-frame sensors, as does Sony’s A9 which also shares a closer specification, enhanced AF with a 2019 firmware update (perhaps a pre-emptive strike?!) and a body that’s smaller and lighter, albeit not as tough. Sony is also hungry for the pro sports and wildlife market and while the A9 is more expensive than the OM-D E-M1X, it’s only by about one third more. While the full-frame sensors in the Canon, Nikon and Sony pro bodies may deliver lower noise at high ISOs, the smaller Four Thirds sensor in the E-M1X with its two-times field-reduction allows relatively small lenses to deliver long effective focal lengths, making for a more compact and lighter system. Of course the proof of the pudding is in the eating which is why I put the E-M1X through an intensive array of tests photographing motorsports, cycling and birds, as well as finding out just how good the weather-sealing is in practice. Everything I know about the OM-D E-M1X can be found in my in-depth video review below, so sit back, relax and find out if it’s the pro action camera for you!

Above: The EM1X sensor is now over two years old and unbelievably it’s only the second camera to use it, but if you’re into shooting action with this system it remains the best option as it’s the only one with embedded phase-detect autofocus. So in terms of photo and video quality and AF hardware, it’s essentially the same as the EM1 Mark II, but Olympus has improved the focusing algorithms as well as the built-in stabilisation, claiming up to 7 stops of compensation with unstabilised lenses or 7.5 with Sync IS models like the 12-100mm.

Above: To put it to the test for stills, I took it around Brighton at dusk, deliberately fixing the sensitivity to a low value and letting the stabilisation deal with the slow shutter speeds. I used the 17mm f1.8 which, with a 34mm equivalent field of view, would normally require a shutter speed of at least 1/30 to avoid shake. With stabilisation enabled though, the EM1X let me easily handhold beyond one second. In fact the slowest shutter I managed to handhold was eight seconds, and that was without leaning against anything. That’s an incredible eight stops of compensation even with my coffee-related wobbles. And that’s one of the benefits of having a smaller sensor – the chance to deliver amazing stablisation which in turn allows you to deploy lower ISOs for decent quality and leave the tripod at home for all but the longest exposures. No-one does this as well as Olympus and it’s also fantastic for video as I’ll show you later.

Above: Water test

Above: With its integrated battery / portrait grip, the EM1X reminds you of the Canon EOS 1Dx Mark II or Nikon D5. But while the EM1X comfortably becomes the largest, heaviest and most expensive camera in the Micro Four Thirds system to date, it’s still roughly half the price of the pro Canon and Nikon DSLRs, not to mention a little smaller and up to a third lighter.

Above: Olympus OMD EM1X top view, see video review for full details.

Above: Olympus OMD EM1X rear view, see video review for full details.

Above: The EM1X is equipped with an electronic viewfinder with a large 0.83x magnification, bigger than most although matched by the Lumix G9. But while most high-end mirrorless cameras already employ 3.68 million dot panels with 5.76 million dot viewfinders already making an appearance, Olympus has opted for a relatively low-resolution 2.36 million dot panel, making its viewfinder image look coarser; you can most obviously see this around the edges of fonts, although it also means very fine details in the frame may look slightly fuzzier than rival viewfinders. Additionally, Olympus has stuck with LCD technology for its viewfinder which, like the EM1 models before it, delivers a lower contrast image compared to the high contrast OLED panels of pretty much everyone else. Olympus chose LCD based on refresh and the fact it believes the softer image is better-suited to skin tones. As a landscape shooter, I personally prefer the punchier OLED panels and haven’t experienced issues with refreshing, but I certainly don’t mind the LCD panel on the EM1X, although I do wish it had been higher resolution, especially for the price. I should also add in both of the continuous Low drive modes, whether using the mechanical or electronic shutter, there’s some viewfinder blackout between frames, although it is possible to follow subjects fairly effectively while shooting. You may also notice the viewfinder resolution drop temporarily while focusing.

Above: Olympus OMD EM1X screen mechanism.

Above: Olympus OMD EM1X touch controls, see video review for full details.

Above: Olympus OMD EM1X battery tray
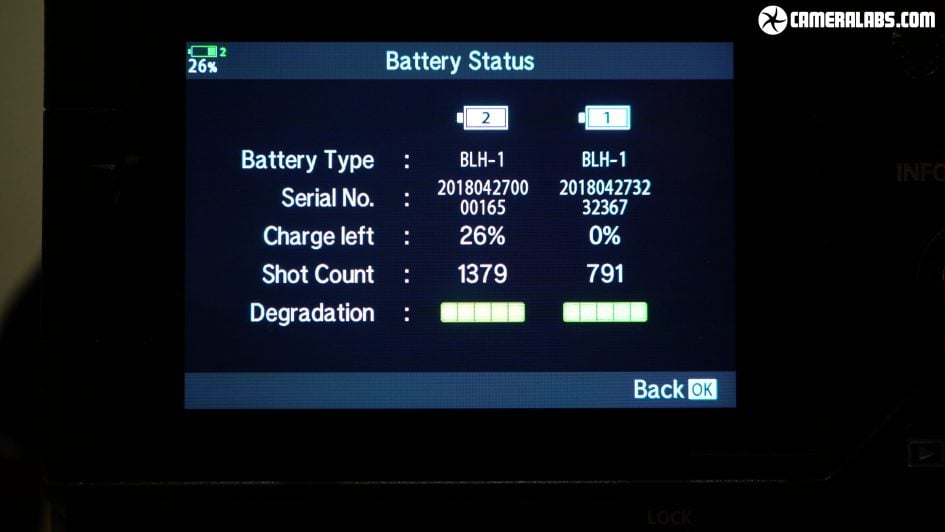
Above: Olympus OMD EM1X battery menu. In terms of video I managed to film just over ten half hour 4k clips in a row, 307 minutes in total with no overheatng, and I also managed to film half an hour of 4k under USB power from my MacBook Pro supply, so long as there was a few minutes of charge in the batteries. Oh, one more thing. When battery 1 is running low, you’ll see the icon flash red even if battery 2 is fully charged and ready. It’s really distracting especially if you’re filming and don’t know if you have enough power to finish the clip. It’d be much better if the E-M1X either displayed the life of both batteries as separate icons like Fujifilm, or added them together into a running total.

Above: Olympus OMD EM1X card slots, see video review for full details.

Above: Olympus OMD EM1X ports, see video review for full details.

Above: Olympus OMD EM1X drive modes, see video review for full details.

Above: Here’s a sequence I shot using Pro Capture, fully pushing the shutter down as the bird took off. Thanks to the pre-buffering while I half-pressed, the EM1X captured a bunch of frames prior to take-off, ensuring I didn’t miss the moment. Panasonic has something similar but at 4 or 6k video resolution and in JPEG only, whereas Olympus captures at the full 20 Megapixel resolution in JPEG or RAW and can autofocus during the burst in the low mode. You won’t find this on any Canon, Nikon or Sony body at the time I made this video.

Above: Olympus OMD EM1X AF areas, see video review for full details.

Above: The AF array may be inherited from the EM1 Mark II but it’s now powered by dual processors running completely redeveloped algorithms. I’m using continuous AF with tracking here and with face and eye detection enabled, which now uses the phase-detect system. It’s still not as sticky as the latest Sonys, but manages to stay with me most of the time.
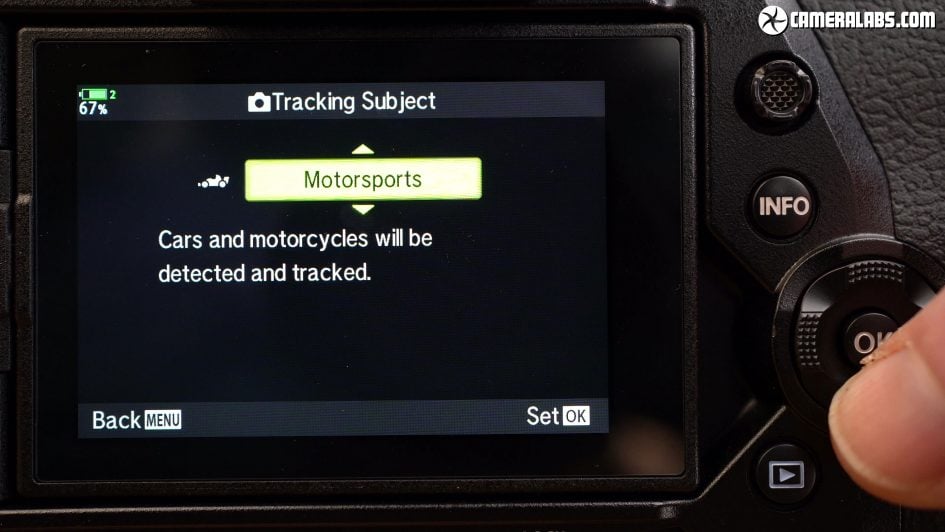
Above: You can choose face with or without eye detection from the menus and I’d recommend enabling it when shooting people, but turning it off when you’re not as it can sometimes mistake other objects for faces and prioritise them. Beyond human faces, you can now tell the EM1X to track three other types of specific subjects: cars and bikes, aeroplanes and helicopters, or trains, and in each case Olympus has trained the system to not only recognise and follow them with an AF box, but also priortise details when they get close enough, like a driver’s face or the front cabin of a long train.

Above: You can see it working here with a radio controlled car, and once the system recognises the object, it’ll surround it with a flexible frame and focus on that.

Above: I didn’t just shoot toy cars though. I took the EM1X to Donington to shoot proper cars on a racetrack and all the photos I’ll show you were taken with the 300mm f4 lens for a 600mm equivalent field of view.

Above: I used the car tracking mode for most of my shots and found the camera successfully locked onto vehicles as soon as they entered the frame, surrounding and following them with a flexible rectangular box. It looks and works like face detection in this regard, only with cars or other vehicles. I do wonder if all of this intelligence could just be wrapped-into a single object tracking mode though. The hardware kept-up, refocusing the lens confidently in either of the continuous Low modes, shooting up to 10fps with the mechanical shutter or up to 18fps with the electronic shutter. If I panned quickly with the electronic shutter there was unsurprisingly some skewing, but it’s not as noticeable as some cameras I’ve tested like the Fujifilm XT3.

Above: Vehicle tracking’s all very well, but what if you’re a wildlife shooter? I headed down to Brighton’s seafront to capture the local seagull population.

Above: In the absence of any specific bird or animal recognition modes, I just used the normal Continuous AF with tracking option for these photos and the 40-150mm at 150mm f2.8 for a 300mm equivalent field of view. Generally speaking the tracking would begin to follow the bird as it approached, but occassionally jumped away, forcing me to restart the tracking again. Don’t get me wrong, it still worked better than many cameras I’ve tested and delivered a decent hit-rate, but again it’s lacks the confidence of the recent Sony cameras I’ve tested.

Above: I then tried the EM1X for cycling, placing the target over Alexander as he cycled towards me. This sequence was shot with the 40-150mm at 150mm f2.8 for a 300mm equivalent field of view, and I used the electronic shutter mode which captured 17-18fps in practice. Like most cameras the challenge is accurately selecting the subject when it’s small and distant, but as it becomes larger on the frame, it’s easy to specify and remain locked-on. I enjoyed using continuous AF with tracking to recompose the shot without worrying whether the bike was under the correct AF area.
Above: Unique modes.

Above: Unique modes

Above: Here’s a sample image I took using the normal and handheld high-res modes, starting with the full image, then magnifiying the normal 20 Megapixel version on the left and the 50 Megapixel composite high-res version on the right. Like its predecessors, the success in real-life situations can vary considerably depending on the subject, your lens, the settings and your technique. Sometimes there would be a dramatic difference in detail on the high-res version, but at other times there didn’t appear to be anything between them. Despite Olympus claiming to better-handle elements of the frame that are in motion, there can still be some undesirable artefacts, particularly on shots including people, birds or cars in motion, or even simply trees or foliage gently swaying in the breeze. On the plus-side, the new handheld mode certainly appears to work, allowing you to capture potentially higher resolution images without a tripod, but since the subjects which benefit the most are studio, archive or architecture, you’ll probably have a tripod on-hand anyway.

Above: ND Shooting – 30th to half a second at 1 EV to 5 EV

Above: To start off, here’s a normal exposure of a seascape without any ND filter, digital or physical – it’s at 200th of a second.

Above: Next here’s the mildest Live ND setting of ND 2 or 1 stop which used a shutter speed of 1/30. Note you need to be in Manual or shutter priority modes to use the Live ND feature.

Above: Now Live ND 4 or 2 stops, which used a shutter speed of 1/15

Above: Next Live ND 8 or 3 stops which used a shutter speed of ⅛

Above: Now Live ND 16 or 4 stops which used a shutter speed of ¼

Above: And finally the strongest setting, Live ND 32 or 5 stops, which used a shutter speed of ½. There’s definitely some blurring in there, but how does it compare to an actual physical ND filter under the same conditions?

Above: Here’s the result with a 3 stop Lee ND filter which as you can see has introduced a mild colour cast, but look beyond it to the motion and blurring. With the sensitivity reduced to 64 ISO, I was able to deploy a shutter speed of 0.8 seconds, a fraction longer than the Live ND 32’s half second, but there’s visibly greater blurring and smoothing on the surface.

Above: Compare it again to the Live ND 8 setting on the left here which simulates the same 3 stops, but using a quicker one eighth of a second exposure. In this example I’d say the physical filter on the right is doing a better job, but the Live ND simulation, especially at its strongest setting is still delivering a useful alternative especially since it’s hassle-free. Seascape photographers will probably stick with physical filters, but for an easy blurring effect on faster motion, like waterfalls, the Live ND mode can be very convenient.

Above: Olympus OMD EM1X custom menu, see video review for full details.
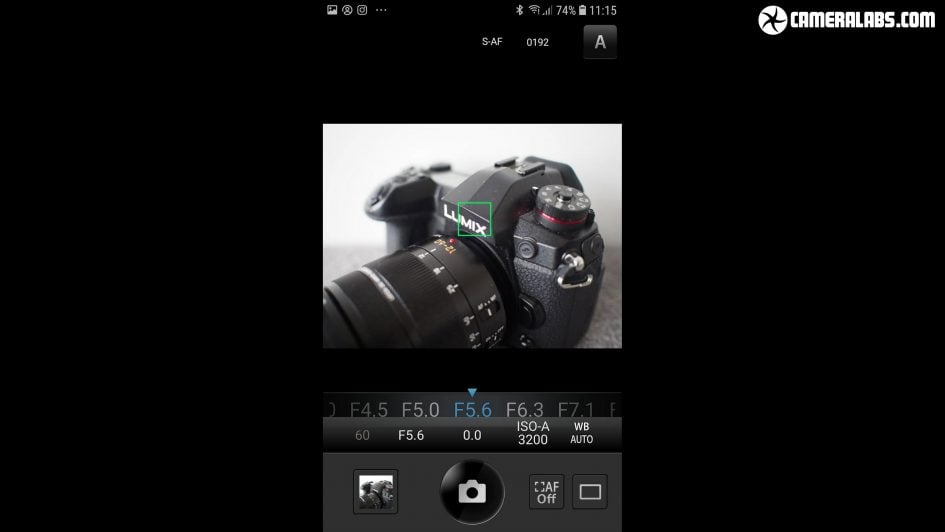
Above: The EM1X is equipped with Wifi and now Bluetooth too, allowing you to easily connect and wirelessly remote control it with your smartphone. I used the Android version of OI Share to remotely shoot and the app lets you tap to refocus stills, change exposure mode, adjust shooting settings and trigger photos or videos.
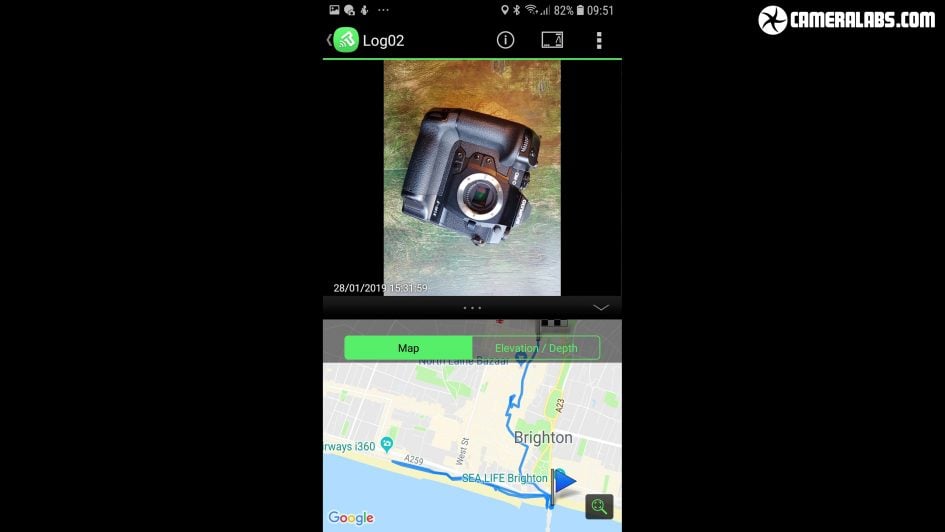
Above: It’s also easy to browse thumbnails of images on the card and copy across the shots you want. Meanwhile the OI Track app can import logs recorded by the camera, graphically displaying your route and elevation change, although if you’d like to also see the photos you shot during the trip you’ll need to manually copy those over as well.
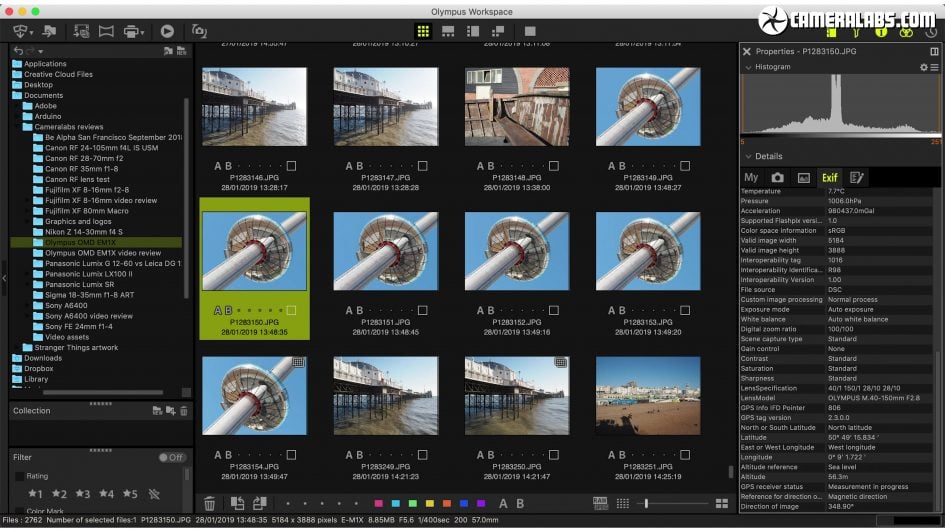
Above: Olympus now also supplies the updated Workspace software for image browsing, management and manipulation; you can also see data from the field recorders at the top and bottom of the EXIF box on the right.
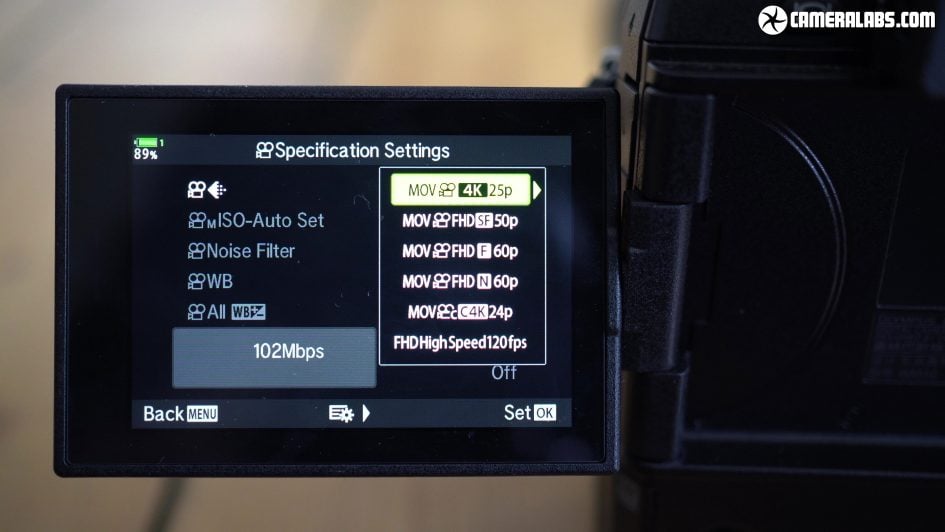
Above: Moving onto video, the EM1X unsurprisingly performs similarly to the EM1 Mark II. As such you can film 1080 or 4k in 16:9 or slightly wider cinema ratios, but sadly it won’t film 4k above 30p which is a shame for a high-end camera in 2019, and also disappointing since the EM1X can capture 60fps bursts at 20 Megapixel resolution and now has double the processing muscle of the EM1 Mark II.
Check prices on the Olympus OM-D E-M1X at Amazon, B&H, Adorama, or Wex. Alternatively get yourself a copy of my In Camera book or treat me to a coffee! Thanks!





