Olympus OMD EM10 Mark III review
-
-
Written by Gordon Laing
In depth
The Olympus OMD EM10 Mark III is a compact mid-range mirrorless camera aimed at photographers who want the flexibility and quality of an interchangeable lens camera without the size and cost of higher-end bodies. Announced in August 2017, it’s the successor to the EM10 Mark II launched two years previously.
The OMD EM10 Mark III is a subtle upgrade to the Mark II, sharing a great deal with its predecessor, including the same 16 Megapixel Micro Four Thirds sensor, the same five axis sensor-shift stabilisation (good for four stops of compensation), the same 2360k dot / 0.62x magnification electronic viewfinder, the same Wifi capabilities, and the same 3in / 3:2 shaped / 1040k dot tilting screen. New to the Mark III is the TruePic VIII processor that equips it with 4k video recording (at 24, 25 or 30p) which also benefits from the sensor-shift stabilisation. The contrast-based AF system has also been upgraded from 81 to 121 points, and continuous shooting improved fractionally from 8.5 to 8.6fps. The body is also slightly larger and a tad heavier, but it remains a very compact camera you’d be happy to carry anywhere.
Overall the Mark III’s upgrades may seem subtle at first glance, but the enhancements to the menus and controls transform its use (especially for beginners), while the addition of 4k brings it up to date. It’s a shame Olympus didn’t take the opportunity to increase the viewfinder magnification or fit a microphone input, but like its predecessor the Mark III remains a great choice for those wanting a compact but friendly, feature-packed and affordable interchangeable lens camera which enjoys access to the broadest mirrorless lens catalogue around – all enjoying the body’s built-in stabilisation. Is this the right mirrorless camera for you? Find out in my in-depth review below!

Olympus OMD EM10 Mark III design and controls
The Olympus OMD EM10 Mark III is a very compact mirrorless camera that perfectly balances retro-styling with modern functionality. Measuring 122x84x49.5mm and weighing 410g with battery, it’s only fractionally larger and heavier than its predecessor and remains one of the smallest cameras around with a fair sized sensor, viewfinder and interchangeable lens mount. Olympus complements it with an equally tiny collapsing 14-42mm kit zoom that adds just 22.5mm to the thickness and 93g to the weight.

Like the Mark II before it though, the EM10 Mark III feels a lot more solid and comfortable than you’d expect for a camera of its size and mid-range positioning. There’s no formal weather-sealing nor tough credentials at this price, but the EM10 Mark III’s build quality feels very solid, dense and reassuring in your hands, and the slightly enlarged grip allows you to hold it securely and comfortably.
I also appreciate how Olympus doesn’t employ tiny controls just because the body’s compact. The earlier EM10 Mark II deployed satisfyingly chunky control and mode dials on the top panel, which the Mark III has refined further, in particular making the mode dial easier to grip. As before, each dial provides very positive feedback when turned and the positions of the two control dials also make them easy to adjust while holding the camera single-handed.
I’ve said it before and I’ll say it again: Olympus nails retro-modern styling better than anyone. Fujifilm’s bodies are arguably prettier, and some may prefer their shutter dials and aperture rings, but I personally fall for the Olympus approach every time. It’s easy to style a digital camera like an old film SLR, but doing so can often compromise modern controls simply for the sake of looks. With the OMD series there are plenty of respectful nods to the classic OM film SLRs – such as the power switch on the Mark III that turns 90 degrees to power the camera on, and in a modern touch, twisting it a little further pops-up the built-in flash – but by sticking with customizable twin control dials it doesn’t suffer from the functional limitations of dedicated aperture and shutter dials. Of course this is a very personal preference, but I love the look and approach of the OMD series. This is how to do retro on a modern camera.
In terms of controls, the EM10 Mark III may appear identical to its predecessor at first glance, but look closer and there’s some important operational differences – mostly for the better. For starters there’s that main mode dial with a larger diameter knurled ring at the top which makes it easier to grip and turn; there may still be no locking button to prevent it turning by accident, but I never had any issues with it, even when removing it from a pocket or tight bag. Eagle-eyed Olympus fans will also notice a slight rearrangement of the modes themselves, along with the dispensing of the Photo Story option for the new AP Advanced Photo Mode which I’ll discuss later in the review.

Around the upper right of the body you’ll find the two Function buttons, flanking the red movie record button. The two Function buttons can be customized to one of eight options, although by default Fn1 operates as an exposure / focus lock and Fn2 toggles the digital tele-converter. Interestingly these are the only two customizable buttons on the EM10 Mark III, considerably less than on the Mark II where virtually every button including the movie record and cross-keys on the rear were customizable. While it’s easy to feel disgruntled by this ‘down-grade’ in potential customization, I don’t feel it’ll impact the target audience. Indeed many, including myself, often felt overwhelmed by the degree of customization on previous models with their perilously complicated custom menus. Now on the Mark III it’s much simpler and better for it.
Speaking of the cross-keys on the rear, the Mark III has permanently assigned them to the most common settings with helpful labels: push up to adjust the ISO, right for the flash options, down for the drive modes and left to adjust the AF area. These may have been unlabeled and customizable on the Mark II, but I think most owners of this body will be happy with Olympus’s strategy here.
One final note about the button on the upper left side by the power switch: previously a third Function button on the Mark II, it’s now dedicated to presenting further options relevant to the particular shooting mode. If you’re in PASM modes, the button fires-up the Super Control Panel which superimposes icons across the entire screen for a wealth of adjustments. In Movie mode, it lets you choose between High Speed, Clips, 4k or normal filming modes. In ART mode it presents the full range of creative filters and their sub-categories. Similarly for the new AP mode, you’ll be shown all the advanced shooting modes. In Scene mode, it lets you choose from a list of categories like People, Motion or Scenery.

If you’re set to full Auto, this button presents the new Shooting Tips menu on-screen. This tray of icons slides out from the right side of the screen, providing quick and easy access to the colour saturation, the colour warmth, brightness, background blur and motion blur, along with a selection of actual short written tips on various types of subjects from children and pets to composition and accessories. It’s also possible to access the tray of icons by tapping a ‘handle’ on the right side of the screen.
I really like how this button provides access to additional options, depending on the mode. It works particularly well in Auto with the Shooting Tips, but is also a handy way of accessing the Super Control Panel in PASM modes, while leaving the OK button to access the simpler options strip down the right side of the screen. These may all be subtle changes to the user interface, but make a big difference in day-to-day operation, especially for the target market.
In terms of composition, the EM10 Mark III is identical to its predecessor, with an OLED viewfinder or a tilting touchscreen. Like the Mark II, the viewfinder employs a 2.36 Million dot / 4:3 shaped OLED panel with 0.62x magnification. In these respects it’s similar to other mirrorless cameras at this price point, although Panasonic is edging ahead on magnification to deliver a larger image at this price point. It is however worth noting all the electronic viewfinders on modern mirrorless cameras deliver a comfortably larger image than the viewfinders on comparably-priced DSLRs, as well as a wealth of shooting information, guides, and the possibility to frame movies and playback photos or video too. I should add that within the mirrorless market, the Micro Four Thirds bodies from Olympus and Panasonic also enjoy the fact most viewfinder panels share the same 4:3 shape as their sensors, so their images fill the full height of the viewfinder versus being presented letterboxed with strips at the top and bottom.

If you prefer to compose with a screen, the EM10 Mark III offers the same 3in / 3:2 shaped LCD panel as the Mark II that’s touch-sensitive and can angle vertically upwards by about 90 degrees or down by about 45 degrees. This vertical tilt is useful for framing at high or low angles in the landscape orientation, but won’t help you if you’re shooting in the portrait / vertical orientation. It’s also unable to flip forward to face the subject, making it much harder to frame selfies or filming pieces to camera; it’s a shame since the movie stabilisation is otherwise ideal for handheld vlogging. If you want a screen that can flip out to the side, angle for portrait or landscape orientation, or face the subject, consider either Panasonic’s Lumix G80 / G85 or the higher-end Olympus OMD EM5 Mark II.
The 3:2 screen shape means images composed or played-back in the native 4:3 aspect ratio are presented with thin vertical bars running down either side. The 1037k dot resolution delivers a detailed view and while, like all screens, it can become trickier to view in direct sunlight, you can angle it up or down a little to alleviate the issue.
As before, you can use the touch screen to easily reposition the AF area, pull-focus while filming movies, navigate the Super Control Panel (albeit not the main menu system), or swipe through images in playback. Like the Mark II before it, you can also enable a Touchpad option in the menus that allows you to drag the AF area with your finger while composing with the viewfinder. It sounds awkward, but actually works really well and I never had an issue with my nose inadvertently moving the AF area by mistake.
In terms of shooting information and guides, the OMD EM10 III cycles through a variety of views using its INFO button, overlaying a live histogram, dual axis leveling gauge, shooting information only, or a clean view. It’s also possible to overlay a selection of alignment grids and lines. In manual focus you can enable focus peaking with or without a magnified view that makes nailing the precise focus a doddle. I’ll discuss this more in the handling section later, but wanted to mention here that the wealth of information, views and guides exceed typical DSLRs and are also available when shooting with the screen or viewfinder.
In terms of ports, the EM10 II is equipped with just two behind a flap on the right side of the body: a Type-D HDMI Micro Connector and a USB-2 port, the latter now mercifully employing a standard socket. Sadly for movie enthusiasts though, there’s still no jack for an external microphone. It’s a slightly odd omission since the Lumix G80 / G85 and Fuji XT20 both have one, but I guess it’s another differentiator with the higher-end EM5 Mark II. The move to a standard USB port also means the Mark III misses out on the optional RM-UC1 remote control release, although you can still control the camera by Wifi using an iOS or Android smartphone if preferred and I’ll detail this process later in the review. Note the USB tethering to a Mac or PC using Olympus Capture software is not supported on the EM10 III – you’ll need to go for the EM5 II or EM1 for that. There’s also no port for a remote cable release, unless you’re using the USB port.
On the top of the EM10 III you’ll find a small popup flash, rated at a Guide Number of 8.2 at 200 ISO, along with a hotshoe to mount external flashguns. Other cameras in its class are also equipped with popup flashes and while they’re all small, I still find them useful for close-range use or fill-ins. I miss their absence on higher-end models like the OMD EM5 Mark II.
The EM10 III is powered by the same BLS-50 Lithium ion battery pack as the Mark II, which has a 1210mAh capacity. Olympus reckons the charge on the BLS-50 should get you around 320 shots with IS enabled or around 80 minutes of pure 4k video, under CIPA conditions. I found the EM10 III generally delivered close to that in mixed-use with some Wifi connections to my phone and a few movie clips.
Like all Olympus OMDs to date, the EM10 III continues to resist the chance for its battery to be topped-up (or even fully-charged) in-camera over USB. Instead when you need to charge your battery, you’ll need the supplied charging unit and an AC socket to plug it into. I know this is the traditional (and still most common) way of doing things, but I find the option of recharging a battery in-camera over USB so much more convenient when I’m travelling or simply out and about as I don’t need to bring the charging unit, nor find an available AC outlet for it. Instead USB charging allows you to top-up using a portable battery, laptop socket, car adapter, or of course any number of AC to USB adapters you or anyone else might have to hand for other devices. Since mirrorless cameras with their 100% electronic composition chew through batteries at a fair clip, I think all should allow in-camera charging over USB, at least as an alternative to a supplied AC charger.
Olympus OMD EM10 Mark III lenses and stabilisation
The Olympus OMD EM10 Mark III employs a Micro Four Thirds sensor and lens mount which, like all OMD and PEN models before it (along with all Panasonic Lumix G cameras), results in a field reduction of two times relative to full-frame systems. So a 25mm lens delivers an equivalent field of view to 50mm on full-frame, and the effective depth of field compared to full-frame is also reduced by two times, so f1.4 on Micro Four Thirds will deliver a depth of field equivalent to f2.8 on full-frame.
The Micro Four Thirds mount gives the OMD EM10 Mark III access to the broadest and most established native lens catalogue of all the mirrorless camera systems. Micro Four Thirds has over 75 lenses available from Panasonic and Olympus along with third parties including Sigma, Tamron, Samyang, Voigtlander and others. So while many rival mirror-less formats are only now beginning to cover most bases with a single lens, Micro Four Thirds typically has two or more options available. Whether it’s Fisheye, ultra wide, fast aperture, macro, super-zoom or good old general-purpose, the Micro Four Thirds catalogue has it covered, and many of them are great quality too – find out more in my best Micro Four Thirds lenses guide.
Depending on region, the EM10 III is most commonly offered in a kit with the EZ 14-42mm f3.5-5.6 kit zoom. This is the same collapsing model sold with the Mark II that measures just 22.5mm thick when powered-down, allowing the EM10 III to become a very compact working camera.
Switch the power on and the lens extends by a couple of centimetres with the camera ready for action in less than two seconds; it’s actually not much different to the cold power-up time with a prime or non-collapsing zoom. The zoom operation on the lens is motorised only, using a spring-loaded ring on the barrel – it’s not as tactile as a mechanically-linked ring, but that’s the price of miniaturisation. Meanwhile a thin ring at the end offers manual focusing and while it’s narrow, the damping makes it a lot more usable than the loose ring on the Sony 16-50mm kit zoom.
You’ll see in my results and gallery pages how it performs and inevitably there’s some compromise in the corners due to its size, but it’s a lot better than the Sony collapsing kit zoom. If you do fancy something classy that still keeps the size down, consider the Olympus 17mm f1.8. I used this lens a lot when testing Olympus bodies and love the combination of small size with the chance to achieve shallow depth of field results, not to mention working in low light without bumping the ISO up too much. Anyway, here’s how the coverage looks with the 14-42mm kit zoom.

Above: Olympus EZ 14-42mm kit zoom coverage on OMD EM10 Mark III
The OMD EM10 Mark III, like all Olympus OMD and PEN bodies, features built-in sensor-shift stabilisation that works with any lens you attach. The EM10 Mark III inherits the same five-axis stabilisation of its predecessor, which in turn took it from the original EM1; in theory this should offer four or five stops of compensation with almost any lens you mount.
To find out I mounted an unstabilised 25mm prime lens (with an effective focal length of 50mm). According to photographic wisdom, this would normally require a shutter speed of at least 1/50 for handholding without camera shake.
On the day, I found I needed a shutter of just over 1/50 to handhold this lens without shake. With the stabilisation enabled, I could match the result a little slower than 1/6, corresponding to around 3.5 stops of compensation. Scale this to wide angle lenses and you can find yourself handholding shots approaching one second without shake, allowing you to shoot in low light without opening the aperture or bumping-up the ISO. As expected, this roughly matches the performance I measured from the OMD EM1 and is slightly-bettered only by the EM1 Mark II and EM5 Mark II.
The results are great-looking images in dim interiors or around the blue hours following sunset or before sunrise without the need for a tripod. Of course the ability to handhold a slow shutter speed isn’t going to help if your subject is moving, but for static subjects it’s an incredibly valuable capability.
Even if you’re shooting subjects that aren’t keeping still though, the stabilisation remains very useful for keeping the image steady as you compose. Even with mid-length telephoto lenses, the image floats eerily on the screen or in the viewfinder, allowing you to very accurately compose without any visible wobbling.
Note the stabilisation in the higher-end EM5 Mark II is even better still, giving it an additional stop of compensation in practice and also the ability to deploy the 40 megapixel composite mode. This is why the 40MP mode is not available on the EM1 or EM10 Mark II or III.
Sensor-based stabilisation is also available when filming video (including 4k) and in my tests it worked very well. There’s two modes: MIS1 uses a combination of sensor-shift and digital stabilisation for the smoothest effect of all, albeit losing a little coverage due to the digital compensation, while MIS2 uses sensor-shift only thereby maintaining the full coverage. I have a number of clips demonstrating it in practice throughout the review, but will start with one I filmed while walking through Brighton’s North Laine area using MIS1 and the 14-42mm kit zoom. See how it’s ironed-out all wobbles, turning the EM10 Mark III into a stabilised shooting rig without any additional accessories.
Above: Download the original file (Registered members of Vimeo only)
Olympus OMD EM10 Mark III focusing and continuous shooting
Like its predecessors, the OMD EM10 Mark III employs a contrast-based autofocus system. Like all contrast-based systems, the camera doesn’t know when the subject is at its sharpest until it’s actually focused beyond it, at which point it reverses direction to return to the optimal position. This hunting process happens very quickly, but inevitably makes it harder for the camera to track subjects in constant motion compared to phase-detect AF systems. On the upside, it’s very accurate for static subjects and has also proven to work well in low light.
Like other recent Micro Four Thirds cameras from both Olympus and Panasonic, the single AF performance on the EM10 Mark III is excellent with the camera snapping-onto subjects quickly and confidently, even in low light or at large apertures with a very shallow depth of field.
The EM10 Mark III’s contrast-based AF system employs a finer array than its predecessor with 121 areas made from an 11×11 grid, versus the 81 area / 9×9 array of the Mark II. As before, these cover most of the frame and you can have the camera automatically choose the most appropriate AF area or pick it yourself either individually or from a 3×3 zoned group.
As before you can adjust the size of a manually-selected AF area if desired, on the EM10 III between 3x, 5x, 7x, 10x or 14x. I generally preferred using the 7x and 10x options for accuracy.
Like all OMD cameras, you can tap the touchscreen to move the AF area wherever you like, again within a region that extends across the entire frame. I personally find this incredibly useful and as described earlier the AF Targeting Pad option lets you use the touch-screen to reposition the AF area while composing through the viewfinder.
A highlight of the Olympus contrast-based AF system is the face detection which goes beyond the usual framing of a human face to also lock-onto the eye and focus on that. As before you can have the camera go for the left eye, the right eye, or best of all, the nearest eye in the shot. And you know what? It really works. I use the nearest eye detection for all my people shots with Olympus cameras and even when using bright primes with a very shallow depth of field, it almost always nails it; the only times it misses slightly are when the subject moves or blinks as you take the shot. It’s brilliant for taking shallow depth of field shots of impatient kids too.
So far so good, but like previous OMD bodies, the contrast-based system struggles when it comes to continuously tracking a subject approaching or receding at speed. The camera’s ability to follow a subject and keep an AF area over them isn’t the issue – it’s the actual technology that then drives the lens to focus on them.
I tested the OMD EM10 III with a variety of lenses, including the kit zoom and the 45mm f1.8 and 75mm f1.8 primes, and found it could just about handle subjects moving at a leisurely speed towards you when set to its lower continuous shooting speed of 4fps; think jogging or slow cycling. But at the faster speed I failed to achieve more than a couple of focused images in a burst. Similarly if the subject was faster, like a bird in flight, the EM10 Mark III really struggled even at its low speed.
The sequence below is typical of a cyclist approaching at fairly modest speed. I set the camera to continuous low speed and fired-off 11 frames in just under three seconds, but only the last three were in focus; I’ve pictured them below. Considering I set the camera to its slower speed and the subject wasn’t particularly demanding, this isn’t a great result.

Above: Olympus OMD EM10 Mark III with 75mm f1.8 at 4.8fps. Below: 100% crops

Panasonic also employs a 100% contrast-based AF system, but enhances its performance by profiling the blurred characteristics of its lenses to better-know how to focus. This DFD technology certainly improves the performance, but still can’t match the confidence of the phase-detect AF systems now being embedded into most of the sensors used by the competition. Buy a modern Sony, Fujifilm or Canon mirrorless camera and you’ll enjoy the benefits of phase-detect autofocus and its ability to continuously autofocus on moving subjects with ease. Olympus also offers phase-detect AF, but only on the flagship EM1 series.
So continuous AF remains a weak-point on the lower-priced Olympus bodies, but this may or may not be an issue for you. If you mostly shoot static subjects, or at least ones not heading towards you at speed, you’ll find it perfectly adequate. Indeed as I mentioned earlier, the EM10 Mark III has very snappy autofocus for mostly static subjects and continues to focus in low light when some rivals have given up. As always, you have to think about what kind of photography you do and which tool will suit you the best.
In terms of Continuous Shooting, the EM10 III offers two speeds: High at 8.6fps and Low at 4.8fps, with Olympus quoting a maximum of 22 RAW files, or unlimited JPEGs while memory remains. The RAW buffer remains the same as the Mark II, although the quoted burst speeds are fractionally quicker than the 8.5fps and 4fps quoted for the Mark II.
To put it to the test I fitted the EM10 III with a freshly-formatted Lexar Professional 2000x 32GB UHS-II card, set the shutter to 1/500 and the sensitivity to 400 ISO. Set to Continuous High and Large Fine JPEG, I fired-off 182 frames in 21.19 seconds for a rate of 8.58fps, and the camera seemed happy to continue shooting. Set to RAW, the camera fired-off a short burst at its top speed, then reduced slightly and seemd happy to keep shooting way beyond its quoted buffer: I managed 136 frames in 19.56 seconds for an average rate of 6.95fps. In terms of speed, the Mark III was a fraction faster than its predecessor in my tests as promised in the specs, but more importantly the buffer and or handling of my fast UHS-II card allowed me to keep shooting for much longer.
So the EM10 Mark III can certainly deliver a high frame rate and over a sufficient period to satisfy most situations, but again it’s let down by modest Continuous autofocusing capabilities which, as explained above, don’t even deliver a full hit-rate at the slower burst speed. This rules it out – or at least makes it frustrating – when photographing subjects moving towards or away from you at speed, but it’s fine for subjects where the action takes place at roughly the same distance – such as skateboard, bike, board or acrobatic tricks.
If you like to manually focus, or use lenses from other systems, the EM10 Mark III offers a number of tools to make your job easier. First is magnified assistance which can be set to kick-in as soon as you turn the manual focusing ring on native Olympus or Panasonic lenses; once in magnified view you can adjust the magnification to 3x, 5x, 7x, 10x or 14x, and also scroll around the frame if required.
The EM10 Mark III also inherits focus peaking from earlier models which surrounds the subject in focus with a choice of red, yellow, black or white highlights, allowing you to quickly identify whether the lens is focused correctly or not. It’s particularly helpful when also working in the magnified view, and it also works fine with third party lenses. Note when using non-native manual focus lenses, you’ll need to assign peaking to one of the function buttons as it won’t start automatically as it does with native ones.
The EM10 Mark III also offers AF / MF hybrid modes where the camera autofocuses with a half-press of the shutter, but allows you to make manual focusing adjustments (again with a magnified view and or peaking if enabled) with a turn of the focusing ring. I found the Single AF + MF mode worked well, using the AF to quickly find the subject before allowing you to fine-tune or confirm if necessary.
It all adds up to a very satisfying manual focusing experience, and I am pleased to report Olympus allows you to use it while filming video.
Olympus OMD EM10 Mark III shooting modes
The OMD EM10 Mark III has a tall and narrow mode dial with very positive clicks between positions; as noted earlier, and a newly enlarged knurled ring around the top. In addition to the traditional PASM modes you can choose from full Auto, ART, SCN, Movie and AP (Advanced Photo) modes. AP mode is the big news here, taking the place of Photo Story on the Mark II, and usefully gathering together a variety of advanced shooting modes that were previously scattered throughout the menus.

When set to AP mode, the EM10 Mark III gives you quick and easy access to the Live Composite, Live Time, Multiple Exposure, HDR, Silent, Panorama, Keystone Correction, Auto Exposure Bracketing and Focus Bracketing options. Previously you’d need to know the menus back to front in order to find all these options and I suspect many owners of earlier models either weren’t aware of them or gave up trying to find them. It’s a clever move by Olympus as while the overall features on offer hasn’t changed a great deal from the Mark II, the ease with which you can now find and deploy them on the Mark III absolutely transforms the camera for beginners and experts alike. The only limitation concerns exposure control as all the AP options employ Program to automatically take care of the aperture and shutter selection; that said, you can shift the Program line using one of the control dials to alter the combination of shutter and aperture if desired. I’ll discuss the various options throughout this section, but start with the exposure basics.
The EM10 Mark III offers the same mechanical shutter speed range as the EM10 Mark II, from 60 seconds to 1/4000 and the shutter sound itself is a satisfying click that’s not too loud. By default the EM10 III employs an anti-shock mode indicated in the drive menu by a diamond icon. This uses an electronic front-curtain and zero second delay to minimise the chance of blurring due to shutter shock – sounds complicated, but this is the best set of technologies for avoiding unwanted vibrations. As before it operates at shutter speeds up to 1/320, beyond which the camera automatically reverts to a fully mechanical shutter. I’m pleased anti-shock is now the default drive mode, meaning you don’t need to find it in the menu and wonder why some options have diamond and heart icons. If you prefer though, the fully mechanical shutter option is still available.
Alternatively if you prefer complete silence you can choose the Silent mode, still indicated by a heart icon, but now moved from its earlier position in the drive menu to its new home in the AP mode. This makes it much easier to find than before, but means you can’t choose the exposure mode to shoot in; now on the Mark III, the Silent mode effectively uses Program only.

As before, the Silent mode employs a fully electronic shutter with the benefit of extending the maximum shutter speed to 1/16000, giving you two more stops of exposure control over the mechanical shutter – handy if you’re shooting with large apertures under bright conditions or want to freeze the fastest action. Electronic shutters are great for silence, avoiding vibrations and achieving fast shutters, but due to the readout speed of most sensors, they’re not suitable when the subject – or camera – are in motion as the image can suffer from undesirable skewing artefacts – something I still noticed on the EM10 III with only modest motion. They can also suffer from banding under some artificial lighting, but if you’re careful they can still prove useful in discreet environments.
I’m pleased to find Olympus rearranging its various drive mode options as on previous models it could get very confusing indeed. Now on the EM10 Mark III, you have the choice of normal or anti-shock modes from the drive menu which you’ll probably set once and leave alone, while the fully electronic silent shutter is now sensibly moved to somewhere it’ll be more easily found. The only limitation again is not being able to choose the exposure mode when exploiting the silent shutter, but I think most people will just select it when they need to be discreet, then revert to the normal / anti-shock modes for general use.
Olympus has also sensibly moved the bracketing options from their previous location in the menus to their new home in the AP mode where you can choose from exposure or focus bracketing. The Mark III may lose the ability to bracket ISO, White Balance and Flash Level offered on the Mark II, but to be honest I don’t know anyone who used them – and more importantly I bet there’s many who gave up trying to find the more useful exposure and focus bracketing options hidden in the Mark II’s menus.
Starting with exposure bracketing, the two and seven frame options of the Mark II have gone, leaving the choice of three frames at 1EV increments or five frames at 0.7EV increments. In a welcome update over the Mark II, the Mark III now sets the drive mode to continuous, allowing you to grab all the frames in a sequence by simply holding the shutter down; unfortunately though, the drive mode menu itself is disabled in this mode, preventing you from selecting a self-timer to deploy the bracketing hands-free. Annoyingly the AP mode isn’t available in the smartphone app, so you can’t use your phone to trigger a bracketed sequence either.

If you’d like the camera to bracket and combine the exposures for you automatically, you could go for the HDR mode, now also accessed from the AP mode. Again this has been simplified from the Mark II, and now only offers two preset options named HDR1 and HDR2. These capture and combine four frames with mild or strong contrast effects; the result is a single composite image, but they can include a RAW file in addition if the image quality is set to RAW+JPEG. Note like the bracketing mode on the Mark III, there’s no way to deploy a self-timer for HDR. Here’s a handheld example using the built-in HDR mode.

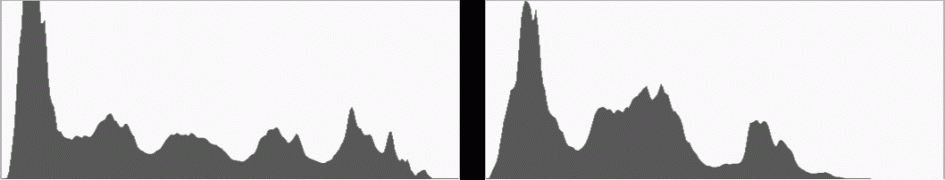
Above left: Olympus OMD EM10 Mark III normal shot. Above right: HDR version
Sticking with the subject of multiple exposures, the EM10 Mark III lets you combine two images on a single frame. This option is again accessed from the AP mode.
Moving on, the EM10 Mark II inherits the interval timer of its predecessor, offering up to 999 frames at intervals from one second to a second shy of 25 hours, and with an initial delay again up to a second short of 25 hours. You can choose whether to record just the images, or have the camera additionally create a movie from them afterwards at 720p, 1080p or in 4k. Note you’ll need to set the photo aspect ratio to 16:9 if you’d like the camera to subsequently encode a widescreen video.
Unfortunately the maximum frame rates inherited from the Mark II reduce the usefulness of the in-camera timelapse movie generation: at 720p, 1080p and 4k, the maximum frame rate offered is 30fps, 15fps or 5fps, so only the first will deliver truly smooth playback. Of course you could simply import the still images into software later to create a timelapse movie at the desired resolution and frame rate, but it’s a shame Olympus can’t generate a timelapse movie in 1080p and 4k at smoother frame rates – it was an annoying limitation of the Mark II inherited here.
Above: Download the original file (Registered members of Vimeo only). The OMD EM10 Mark III offers timelapse capabilities which can assemble photos into a movie afterwards, but they seem unchanged from the models before it. As such you’ll only enjoy smooth frame rates if you encode your movie at 720p. If you want 1080p, the maximum frame rate falls to 15fps (as demonstrated above) and if you want a 4k timelapse, it falls further to a paltry 5fps. This is poor show compared to much cheaper Panasonic Lumix bodies which have offered smooth 4k timelapses for ages. Olympus needs to update this part of its software to be more in-line with the camera’s other video capabilities. In the meantime for the clip above I captured 300 frames at one second intervals in Aperture Priority and again chose the 1080 / 15fps option as a balance between smoothness and resolution.
On the upside, the EM10 Mark III also inherits the handy and unique options for long exposure fanatics. First is the ability to dial-in a shutter speed as long as 60 seconds in Manual, which is often long enough for basic long exposure work without the need for any accessories. Panasonic also offers this on its Lumix G cameras, and I find it invaluable.
Turn the exposure dial beyond 60 seconds in Manual mode and you’ll be offered Bulb followed by Live Time and Live Comp, the latter introduced on the EM5 Mark II. Bulb works the same as a normal camera with the shutter staying open for as long as you have the release held down. Live Time is more considerate for those without accessories as it opens the shutter with one press of the release and keeps it open until you press it again – so you don’t need to keep the button held down throughout the entire exposure.
Of course for the best results you’ll not want to touch the camera to start and stop a long exposure, and while the Mark III sadly loses the ability of its predecessors to either deploy a self-timer or an anti-shock delay to start an exposure hands-free, you can still preset the total exposure length. You can set the maximum exposure time to be 1, 2, 4, 8, 15, 20, 25 or 30 minutes, after which the camera will automatically end the exposure.
What makes the Olympus cameras even more unique though are their Live Bulb and Live Time options which let you take regular peeks at the exposure on the screen as it builds-up to see how it’s getting on. This lets you stop the exposure early if it’s already perfect, or perhaps not going to work out. The interval between updates can be set to 0.5, 1, 2, 4, 8, 15, 30 or 60 seconds, and the maximum number of peeks depends on the ISO value: 9, 14, 19 or 24 times for ISOs of 1600, 800, 400 or Low respectively. Once you’ve used up your allocation of peeks, there’ll be no more, regardless of the exposure length. You can find the options to configure this in Custom section D2.
During a long exposure, the actual exposure time is displayed like a digital stopwatch whether the Live update is enabled or not. If the Live update is enabled, then the screen will also show the image gradually appearing – like a developing photo – along with a brightness histogram that provides accurate feedback on the tonal range as it builds. The histogram updates its graph for every scheduled peek and it’s great fun to see it gradually move from left to right, filling the shadows, then the mid-tones and finally the highlights during a long exposure. The histogram is useful because the screen – especially when viewed in the typically dark conditions of a long exposure – is not always an accurate representation of the image. If you’re remotely controlling the camera over Wifi you can even view the mid-exposure peeks on your phone’s screen.
The ability to peek at a long exposure while it’s being recorded is innovative, fun and genuinely useful, but be aware it can come at the cost of slightly increased noise levels. That said, the impact is minor and it’s also the type of noise that’s effectively reduced in post-production if necessary.
Further extending the Live Time concept on the EM10 Mark III is the Live Comp mode, which you’ll find after Bulb and Live Time in Manual. This addresses the problem of long exposure photography where one portion could become over-exposed before another has started to register, or even appeared at all. For example when shooting fireworks, you may want to have the background nicely exposed, but it could become over-saturated as you wait for the perfect explosion. The same thing can happen when you’re light-painting. Wouldn’t it be nice to effectively stop one part of the exposure while you wait to complete another part?
Photographers have traditionally done this by taking two or more exposures and compositing them later, but the Live Comp mode attempts to do this entirely in-camera. First it exposes for the background, then it waits for any new light to appear in the composition. When new light does appear, such as a fireworks explosion or a new light painting, the camera will resume the exposure, but crucially only in the area where the new light is. This allows the frame to record the new area of light, without affecting the existing exposure underneath.
Here’s an example of Live Comp used for light painting, which I took at an Olympus event using the earlier EM5 Mark II, although the functionality is essentially the same here; the artists were Zolaq. The mode was set to a five second cycle at f8 and 100 ISO, and the entire process took about five minutes to complete.

Above: Olympus OMD EM5 Mark II Live Comp
Live Comp and Live Time can be a little intimidating at first, so the EM10 Mark III now offers additional simpler versions with fewer options from the AP menu if preferred.

Switch the mode dial to SCN and you can choose from a selection of presets, arranged in six groups, albeit with some duplication within some categories: People offers five options including nightscape and skin-enhanced modes, Motion offers three options including sports and panning effects, Indoor offers six options some of which are borrowed from the People and Motion categories, Nightscapes offers five including light trails, Scenery offers four including sunsets, and Closeups offers four including documents and focus bracketing.
Moving on, the ART position on the dial lets you apply a selection of 15 different filters: you can choose from Pop Art, Soft Focus, Pale Light and Colour, Light Tone, Grainy Film, Pin Hole, Diorama (Miniature), Cross Process, Gentle Sepia, Dramatic Tone, Key Line and Watercolour, Vintage, Partial Colour and new to the Mark III over its predecessor, Bleach Bypass. Each of these has two or more options, bringing the effective total of effects to 30. Pressing the OK button lets you access the main 15, while pushing the button to the left of the power switch presents access to all 30.
The good news is unlike many rivals, Olympus continues to support recording in RAW+JPEG mode with ART filters, applying the effect to the JPEG, but leaving the RAW untouched in case you later decide for a different effect or none at all. Shooting in RAW is a sensible option too as you can generate new JPEGs with different ART filters applied during playback if desired, allowing you to explore alternative options after the event, or of course deciding not to bother at all if they don’t suit the subject after all; the ART bracketing option in RAW processing during playback lets you generate more than one at once too. Here’s some of the ART filters in action

Above left: Pop ART filter. Above right: Pale ART filter

Above left: Pinhole ART filter. Above right: Cross Process ART filter

Above left: Dramatic Tone ART filter. Above right: Keyline ART filter
The EM10 Mark III also inherits the Keystone Compensation option of recent models which provides real-time correction of converging lines as you compose, although on the Mark III you’ll now find it on the AP menu. There’s nothing stopping you from performing similar skewing after the event, but Olympus likes to offer the chance to do it in the field and I appreciate the chance. Inevitably there’s some cropping of the image and juggling of pixels, but it’s nice to be able to make these corrections in-camera as you compose. Here’s a handheld before and after shot to show you the kind of thing that’s possible with a wide lens pointing upwards taken from exactly the same position, and with the same lens and focal length.


Above left: without Keystone correction. Above right: with Keystone correction
Also on the AP menu is the Panorama mode, but before you get too excited, this still doesn’t auto-assemble a bunch of images captured in a sweep. Instead, Olympus seems stuck in a time warp, offering nothing more than guide lines on-screen, helping you to take one photo at a time, then leaving you to assemble them in your own software later. It’s in stark contrast to the auto panoramas long-standard in models from Panasonic, Sony and Fujifilm. That said, if it makes you feel any better, Canon has only just started offering in-camera stitching.


Above: Panorama stitched using Adobe Photoshop CS6
But there’s better news at the end of the AP menu where you’ll find Focus Bracketing, first introduced on the EM10 Mark II. This allows you to take multiple shots with the camera slightly adjusting the focusing distance for each. The idea is to subsequently combine these in (your own) software to extend the effective depth of field, or the amount that’s in focus. The process of focus bracketing and focus stacking is most popular in macro photography where at extremely close distances the depth of field is often too small to render the subject sharp from front to back. You could gradually close the aperture, but doing so will increase the effect of diffraction (making the image soft) and may not even cover the desired range. But by capturing strips of sharp focus at different distances, focus bracketing and subsequent stacking can render the entire subject in sharp focus.

The earlier EM10 Mark II offered a wealth of configuration options, including the number of frames from 3 to 999, and the focus differential from one to 10. Now on the Mark III it’s much-simplified: the camera will take eight frames, no more, no less with just the choice of whether the change of focus between shots is large or small. The goal remains the same as before though, to attempt to capture a sequence where the first and last frames are focused on the nearest and furthest points you’d like to be in focus, while also including a bunch inbetween. These should then be loaded into third-party software for assembling.
Here’s three images I took of a simple macro still life arrangement using the EM10 Mark III and the Olympus 14-42mm kit zoom at 42mm.

Above: The first image is a single frame taken at f5.6 and the band of sharp focus is fairly narrow.

Above: To increase the depth of field you can simply close the aperture down, but doing so will gradually soften the image due to diffraction and you may not still have a sufficiently large depth-of-field to cover the desired range of distances. The shot above was taken at f11.

And so to the focus-stacked version above, consisting of eight frames captured using the smaller differential option, while the lens was set to f5.6 to avoid diffraction. I imported the frames into Helicon Focus (optional stacking software) and found the default Depth Map gave the best results.
Focus Stacking is a fun feature on the EM10 Mark III and certainly a lot quicker and easier than adjusting a lens manually, not to mention more convenient than tethering a camera to a computer to perform the process for you. Olympus has also sensibly simplified the process over the Mark II with much fewer options, but sadly you’ll still need third party software to assemble them into a single image. In contrast, the flagship EM1 can assemble small bunches of stacked images like these in-camera. I wonder how many owners will end up using the feature on the EM10 Mark III?
Olympus OMD EM10 Mark III Wifi
The EM10 Mark III is equipped with Wifi which allows you to wirelessly transfer images and remote control the camera using a free app on iOS or Android smartphones, or tag photos with a GPS log, again made by the app on your phone. The implementation, as far as I could see, was the same as on the EM10 Mark II.
To get started, install the free Olympus Share app on your phone or tablet; it’s available for iOS or Android devices and I tested the latter on my Samsung Galaxy S7. Next tap the Wifi icon in the top left corner of the screen (you may need to press the info button to see it), then the EM10 Mark III will display a QR code on-screen.
Next simply start the Olympus app, choose Easy Connect from the bottom of the screen, and use your phone’s camera to scan the QR code. Almost instantly the phone will have the network and password details in order to connect, and if all goes well, the app should find the camera in the future. But even if you need to go through the QR scanning process each time, it’s almost as quick as holding the devices together for an NFC negotiation. Only Bluetooth is more convenient and I hope Olympus can implement it in the near future.
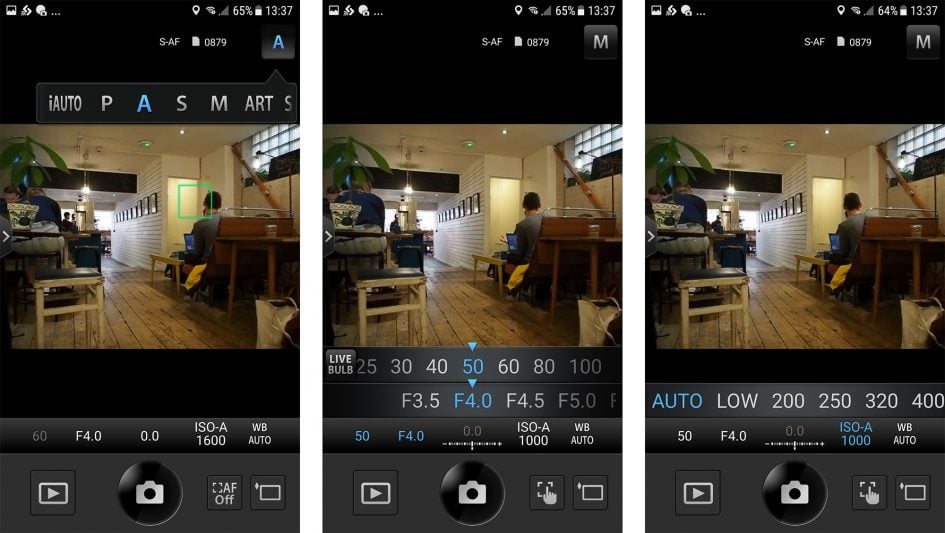
Once connected the Olympus app offers four main options: Remote Control, Import Photos, Edit Photo and Add Geotag. I’ll cover each in turn. Tapping Remote Control lets you see a live image from the camera and refocus it by tapping on your phone or tablet’s screen; if you have a motorised zoom like the 14-42mm kit lens, you can also remote control its focal length using a popout slider.
Impressively you can remotely change the exposure mode between Program, Aperture Priority, Shutter Priority, Manual, iAUTO, ART and movie without touching the camera’s mode dial, although sadly the app hasn’t been updated to offer the new AP mode on the Mark III. Depending on the selected mode, you can then tap to adjust the shutter speed, aperture, exposure compensation, ISO and white balance, along with changing the drive mode, and of course triggering the exposure. If desired you can also dial the shutter speed in Manual all the way to Live Bulb, Live Time and Live Composite, and if previews are enabled on the camera you can view the exposure build on your handset’s screen accompanied by a timer, albeit not a histogram.
The app also allows you to configure a basic interval timer or trigger a movie recording. The interval timer is more like an advanced self-timer, but it’s still a handy feature, and you can also configure it to capture bursts or movie clipss instead if preferred. If you choose to record movies remotely with the camera you can’t touch the screen to reposition the AF area or pull-focus – something that is possible on many rivals, including Panasonic Lumix G models. It’s also not possible to trigger a 4k recording, only 1080p is available.
The second option on the app is to Import Photos and pressing it displays a thumbnail view of the card’s contents which you can scroll through. Tapping a photo displays it full-screen, after which you can pinch to zoom-in for a closer look, albeit not at the maximum resolution. If you like what you see you can save the image to your handset by tapping the download icon, or share it using the sharing icon alongside – of course once it’s saved onto your handset you can also share it later. In the separate settings page you can choose to import images for saving or sharing at 1024×768, 1600×1200, 1920×1440, 2048×1536 or their original resolution. I had no problem copying JPEGs from camera to phone, although RAW files aren’t displayed in the thumbnail view.
Choosing Edit Photo lets you perform a number of adjustments on images that have already been copied onto your handset. You can apply Art Filters, superimpose text, logos, even signatures written on your phone’s touchscreen, and play around with composite Photo Story arrangements.
Finally the Add Geotag option does what it says on the tin by tagging photos with positional information recorded by your phone. For this to work, you first need to switch on the Geotag feature from the app, and if desired, change the logging frequency from the default 60 seconds. After that the app will dutifully record your position at the preset intervals until you’re ready to sync them with the images on the camera.
The actual tagging is a very easy process: if it’s enabled the app will actually offer to tag your photos as soon as the phone and camera are next connected over Wifi. The process is fairly quick too, and the app can additionally plot a log on a Google map, although you may need to disconnect from the camera to load the map details from the internet.

In the example above I embedded the position of this scene from London’s South Bank using the Geotag option, then entered the co-ordinates into Google maps. Like other GPS solutions which rely on your phone, you’re at the mercy of the accuracy of that device – I found my phone generally maintains an accurate position when carried in my pocket, but for absolute accuracy during a shoot you may prefer to keep your phone in the top of a backpack.
Olympus OMD EM10 Mark III movie mode
In an important upgrade over its predecessor, the OMD EM10 Mark II can now film 4k video, in the UHD format. You can film 4k at 24, 25 or 30p, all encoded at the same 102Mbit/s as the flagship OMD EM1 Mark II. Alternatively you can film 1080p at 24, 25, 30, 50 or 60p, although sadly nothing faster for fans of slow motion. Like its predecessor, the EM10 Mark III can also generate in-camera timelapse videos at 720p, 1080p or 4k, but like that model only at maximum frame rates of 30p, 15p or 5p respectively.
To compare the quality between 1080p and 4k on the EM10 III, I filmed the same subject with the Olympus 17mm f1.8 lens closed to f4 in both movie formats. The full view is shown below with the outer edge of the red frame indicating the crop when filming video in 1080p or 4k. Below this are 100% crops taken from screengrabs of the footage.

Above: outer edge of red frame indicates video crop on full image. Below are 100% crops from 1080p (left) and 4k (right) footage.

There’s the choice of two stabilisation modes: MIS-1 uses both sensor-shift and additional electronic stabilisation with a mild crop as a result, while MIS-2 uses sensor-shift only with no reduction in the field-of-view. So when shooting movies in MIS-2 (or no stabilisation) in any quality, you’ll enjoy the full horizontal coverage of your lenses, albeit with a vertical crop for the 16:9 shape. Note the movie stabilisation options are set separately to the still photo stabilisation options.
You can film in Program, Aperture and Shutter Priority or full Manual. In PAS modes the ISO sensitivity is set automatically, but in Manual you can set the sensitivity yourself; sadly there isn’t an Auto ISO option when the movie exposure mode is set to Manual though.
You can set the focus to single or continuous, the latter supporting focus-pulling using the touch-screen. Focus peaking is also supported while filming which makes manual focusing much easier.
Audio is recorded using the built-in microphones only – sadly there’s still no external microphone input on the EM10 III. The maximum clip length is a second shy of 29 minutes, strangely a minute less than most other cameras. Now for a selection of clips to demonstrate the quality in practice.
Above: Download the original file (Registered members of Vimeo only). I also have a version filmed in 1080p for comparison – see my Olympus OMD EM10 Mark III movie sample 1080p.
Above: Download the original file (Registered members of Vimeo only)
Above: Download the original file (Registered members of Vimeo only)
Olympus OMD EM10 Mark III quality
Now it’s time to check out the quality of the EM10 Mark III in practice. Check out my Olympus EM10 Mark III sample images, or my quality page, or head straight to my verdict – all using the tabs at the top of your screen!
Check prices on the Olympus OM-D E-M10 Mark III at Amazon, B&H, Adorama, or Wex. Alternatively get yourself a copy of my In Camera book or treat me to a coffee! Thanks!

 The Olympus OMD EM10 Mark III is a compact, friendly, affordable and feature-packed camera that'll satisfy beginners and more advanced photographers alike. It may at first glance appear to be a fairly minor refresh over its predecessor, the EM10 Mark II, but the upgrades greatly enhance what was already a very compelling camera. The Mark III not only gains very respectable 4k video, but now presents its wealth of advanced shooting modes in a much more accessible manner. Meanwhile it inherits the Mark II's viewfinder, tilting touchscreen, built-in stabilisation and excellent controls. The weaknesses remain the same too: it struggles to stay focused on fast subjects and the 16 Megapixel resolution sounds dated. If you mostly shoot static subjects though, the autofocus is fine, and the resolution is sufficient for most situations. So for general day-to-day photography, the OMD EM10 Mark III is hard to beat for the money. It's an attractive camera that's enjoyable to use and delivers great results in most situations with ease, while offering plenty of room to grow.
The Olympus OMD EM10 Mark III is a compact, friendly, affordable and feature-packed camera that'll satisfy beginners and more advanced photographers alike. It may at first glance appear to be a fairly minor refresh over its predecessor, the EM10 Mark II, but the upgrades greatly enhance what was already a very compelling camera. The Mark III not only gains very respectable 4k video, but now presents its wealth of advanced shooting modes in a much more accessible manner. Meanwhile it inherits the Mark II's viewfinder, tilting touchscreen, built-in stabilisation and excellent controls. The weaknesses remain the same too: it struggles to stay focused on fast subjects and the 16 Megapixel resolution sounds dated. If you mostly shoot static subjects though, the autofocus is fine, and the resolution is sufficient for most situations. So for general day-to-day photography, the OMD EM10 Mark III is hard to beat for the money. It's an attractive camera that's enjoyable to use and delivers great results in most situations with ease, while offering plenty of room to grow.



