Viltrox AF 24mm f1.8 review
-
-
Written by Thomas
Intro
The AF 24mm f1.8 from the Chinese manufacturer Viltrox is a wide-angle prime lens designed for mirrorless cameras and corrected for full-frame sensors. 24mm is a popular focal length for architecture, large interiors and landscape photography without being prone to some of the distortions that a 20mm lens can produce. On a cropped sensor the angle of view is equivalent to a 36mm lens which is often used for street photography. The lens features a relatively bright f1.8 focal ratio and is one of four prime lenses from Viltrox which can autofocus on Nikon Z-mount cameras – the others being the AF 85mm f1.8 II, AF 50mm f1.8, and AF 35mm f1.8. The lens is also available in Sony E-mount. To my knowledge these are the first – and currently only – third-party lenses for Nikon Z-mount with autofocus. The Viltrox AF 24mm f1.8 is made in China and was announced in August 2021. It costs around 395 EUR / 379 USD / 375 GBP.
For this review I tested the Viltrox AF 24mm f1.8 on the 45MP Nikon Z7 camera to judge optical performance and quality of autofocus against the Nikon Z 24mm f1.8 S. I also included comparisons with the Sigma 24mm f2 DG DN (available for Sony and L-mount mirrorless cameras). So if you’re interested in whether this inexpensive wide-angle lens is right for your Nikon or Sony mirrorless camera, you’ve come to the right place!
Facts and features
As usual I’ll have a look at the technical data of the new Viltrox AF 24mm f1.8 first. I’ve rated the features with a [+] (or [++]), when it’s better than average or even state of the art, a [0] if it’s standard or just average, and [-] if there’s a disadvantage. For this comparison I use the Nikon Z 24mm f1.8 S (“Z-Nikkor” for short) and Sigma 24mm f2 DG DN (“Sigma”).
Size (diameter x length): 71 x 82mm (2.8 x 3.2in.). The lens hood adds 26mm and is 77mm in diameter. This is shorter than the Z-Nikkor at 78 x 97mm + 34mm lens hood but the Sigma is even shorter at 70 x 72mm + lens hood. [0]
Weight: 381g (13.4 oz.) plus 18g for the lens hood: The Z-Nikkor is 447g + 23g lens hood, the Sigma is 365g + lens hood. [0]
Optics: 11 elements (including 6 special dispersion and 2 aspherical) in 9 groups. The Z-Nikkor is a 12/10 design, the Sigma is 11/9. [+]
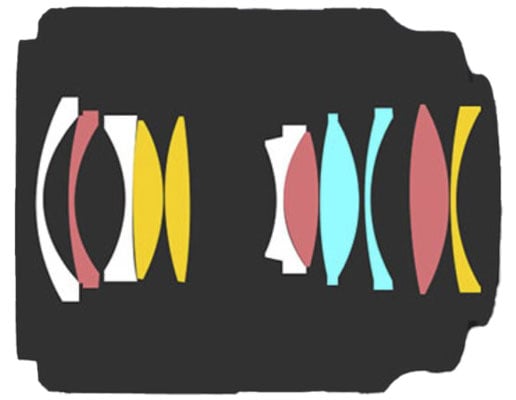
Closest focus distance in manual focus is 0.29m (0.95ft.) with working distance of 0.19m and a magnification of 1:8.9 which is a bit disappointing. A magnification of 1:10 is achieved at 0.32m giving a working distance of 0.2m with the lens hood attached The maximum magnification of the Z-Nikkor is 1:5.7, the Sigma achieves 1:6.7. [-]
Filter-thread: 55mm on the Viltrox, the Z-Nikkor has 72mm, the Sigma 62mm. [+]
Image stabilization: The lenses in this comparison don’t have optical stabilization. You only get the built-in sensor-shift stabilization which most modern mirrorless camera bodies provide. [0]
Auto focus: Yes with built-in AF drive. Manual-focus override is by simply turning the focus ring (unless you’ve assigned a different task to this mulit-function ring). The focus ring has the usual variable gearing similar to the Z-Nikkor and Sigma. [+]
There’s a type C “USB upgrade port” on the lens mount to update the firmware, see below (shows the AF 50mm f1.8). The lens came with firmware v1.0.7 which was the latest version at the time of testing. Their Nikon Z lens mount is not up to specs, again: When you turn the lens fully to unmount it won’t come off – just turn it a bit back to get the lens off the camera body. [0]
Covers full frame/FX or smaller. Same with the alternatives. [+]
Price: The lens is priced at around 395 EUR (incl. 19% VAT) / 379 USD / 375 GBP but I’ve already seen prices as low as 330 EUR after rebates. The Z-Nikkor currently goes for about 999 EUR / 997 USD / 871 GBP, the Sigma is at 600 EUR / 639 USD / 549 GBP. [+]
Comes with a soft pouch and the lens hood is included, reversible for transport. That’s similar to the Z-Nikkor. The Sigma comes without a pouch. [0]
Aperture ring: The Viltrox, like the Z-Nikkor, has a multi-function control ring which can be assigned by the Nikon Z camera to operate the aperture, exposure compensation, ISO sensitivity, focus – or simply switched off. But on the Viltrox there is also a dedicated aperture ring with 1/3 stops (without clicks) from f1.8 to f16 and a position “A” for aperture control from the camera. The Sigma has a similar dedicated aperture ring but with click-stops. Turning the multi-function control ring on the Viltrox other than in focus mode reveals a pretty aggressive gearing: Even small turns of the ring result in large changes in aperture, exposure compensation or ISO. This works much smoother on the Z-Nikkor. [+]
Sealing: No, the Viltrox doesn’t even have the rubber grommet at the lens-mount which the Sigma offers. The Z-Nikkor has further special weather-sealing throughout the construction. [-]
At a score of 2[-]/5[0]/6[+] the lens has no outstanding features – except for its low price and the dedicated aperture ring. But the Viltrox does not offer basic weather protection at the lens mount plus its maximum magnification of 1:8.9 is a bit disappointing.
Focus
Focus accuracy and repeatability is critical to consistently produce sharp shots especially with large aperture lenses. Repeatability (the accuracy of focus on the same subject after repeated focus-acquisition) of this lens was measured 95.7% in Reikan FoCal in initial testing while the Z-Nikkor was at 99.0%. There was no outlier over a series of 40 shots on the well lit and contrasty focus test target but I found that results depended a bit on whether the lens was coming from infinity or from closer. I decided to let FoCal determine whether the lens needed some AF fine-tuning – and it did: After setting a value of -2 for AF fine-tune repeatability/consistency of AF improved to 98.9%.
Regarding focus speed: The Viltrox focuses in around 0.5 sec from infinity to 0.32m (1:10 magnification) – which is comparable to the Z-Nikkor. There was no hunting under the well-lit test conditions. The focus ring (which also can be assigned other tasks by the Nikon Z camera) is 32mm wide. Its surface is not rubberized and feels a bit too smooth for my liking.
AF-operation of the Viltrox is barely audible from the outside or if you record video with the built-in microphone. But operating the aperture ring gave a scraping noise: This is obviously an individual glitch on my copy of the lens as it worked smoothly on the AF 50mm f1.8. As you pull-focus, you’ll notice pretty little focus breathing: the image became only 1-2% more magnified when I adjusted focus from infinity to 0.32m. This is barely visible when shooting videos.
Next check out my quality results!
Check prices on the Viltrox AF 24mm f1.8 at B&H or Adorama. Alternatively get yourself a copy of my In Camera book, an official Cameralabs T-shirt or mug, or treat me to a coffee! Thanks!
 The Viltrox AF 24mm f1.8 is a decent large aperture wide-angle lens with autofocus for Sony E-mount and Nikon Z-mount. It is sharp in the center and offers quite some detail in the FF/FX-corner. But its relatively soft rendering between 8mm and 16mm image height requires stopping down to f5.6 to produce sharp landscapes or architecture shots. The lens offers a dedicated aperture ring, has minimal focus breathing, fares relatively well in contra-light situations, and has a fast and consistent AF - after some AF fine-tuning. Bokeh is nice (for a 24mm f1.8 lens) on less contrasty backgrounds but it can produce ugly double contours in the distance and onion rings on specular highlights. The lens also lacks any form of weather sealing and has strong distortions which are not easily corrected. But all-in-all the lens has a good price/performance-ratio and I can recommend the Viltrox AF 24mm f1.8 if you're looking for a lower-cost wide-angle lens.
The Viltrox AF 24mm f1.8 is a decent large aperture wide-angle lens with autofocus for Sony E-mount and Nikon Z-mount. It is sharp in the center and offers quite some detail in the FF/FX-corner. But its relatively soft rendering between 8mm and 16mm image height requires stopping down to f5.6 to produce sharp landscapes or architecture shots. The lens offers a dedicated aperture ring, has minimal focus breathing, fares relatively well in contra-light situations, and has a fast and consistent AF - after some AF fine-tuning. Bokeh is nice (for a 24mm f1.8 lens) on less contrasty backgrounds but it can produce ugly double contours in the distance and onion rings on specular highlights. The lens also lacks any form of weather sealing and has strong distortions which are not easily corrected. But all-in-all the lens has a good price/performance-ratio and I can recommend the Viltrox AF 24mm f1.8 if you're looking for a lower-cost wide-angle lens.






