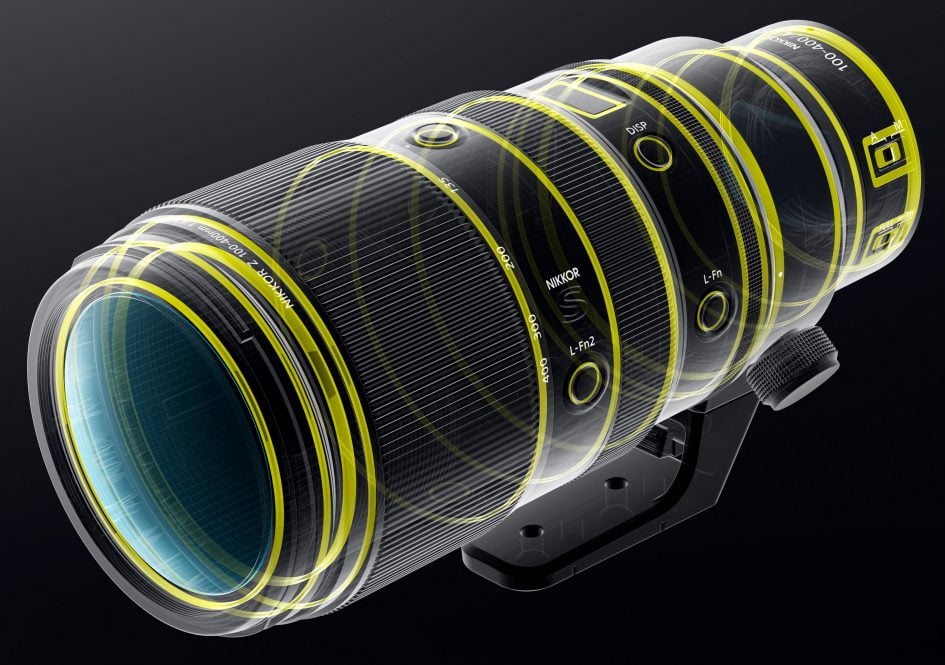
Nikon Z 100-400mm f4.5-5.6 review
-
-
Written by Thomas
Intro
The Nikon Z 100-400mm f4.5-5.6 VR S is a long telephoto lens with a 4x zoom range. It is the first lens for Nikon’s Z-mount mirrorless cameras reaching beyond 200mm focal length and only the second lens which can use Nikon’s Z 1.4x and 2.0x teleconverters. It is corrected for full-frame cameras but can also be used on a cropped body like the Z fc or Z50 where it delivers a field of view equivalent to 150-600mm focal length. The new lens offers optical image stabilization, autofocus, focus limiter, removable tripod foot, additional function buttons, plus an OLED display to indicate aperture, focal length, or focusing distance and depth-of-field. It is the successor to Nikon’s AF-S 80-400mm f4.5-5.6G ED VR which was introduced in 2013 and still can be used via FTZ adapter on Nikon’s Z cameras.
The Nikon Z 100-400mm f4.5-5.6 VR S is made in Japan and costs 2999 EUR / 2700 USD / 2699 GBP.
Facts and features
Let’s compare the Nikon Z 100-400mm f4.5-5.6 VR S (“Z 100-400” for short) to the Nikon AF-S 80-400mm f4.5-5.6G ED VR (“F-Nikkor”) and the Nikon Z 70-200mm f2.8 VR S (“Z 70-200”). The latter can be used with Nikon’s 1.4x and 2x Z teleconverters to become a 98-280mm f4.0 or 140-400mm f5.6 zoom lens. As usual I’ve rated the features with a [+] (or [++]), when it’s better than average or even state of the art, a [0] if it’s standard or just average, and [-] if there’s a disadvantage.
Size (diameter x length): 98 x 222mm (3.9 x 8.7in.). Add 65mm for the lens hood and 49mm when zoomed in to 400mm focal length. The F-Nikkor is 96 x 203 mm + 88mm lens hood + 57mm when zoom-in. Add 30mm for the FTZ adapter to use it on a Nikon Z camera and you end up with a total maximum length of 378mm. The Z 70-200 is 89 x 220mm + 56mm lens hood and does not extend when zoomed in. Add 19mm resp. 33mm for the TC-1.4x or TC-2.0x. [0]
Weight: 1355g (2.99 lb.). Add 63g for the plastic lens hood and 82g for the tripod foot. The F-Nikkor is 1470 g + 95g lens hood + 92g for the tripod ring. Add another 133g for the FTZ adapter to use it on a Nikon Z camera. The Z 70-200 is 1359g + 63g lens hood + 82g tripod foot. Add 220g for the TC-1.4x, 265g for the TC-2.0x. [0]

Optics: 25 elements in 20 groups including 8 special dispersion elements but no aspherical element. The lens has “ARNEO” anti-reflective coating in addition to Nikon’s Nano-coating to reduce flare, glare and ghosting plus fluorine-coating on the front element to repel water, dust, and dirt and make cleaning easier. The F-Nikkor has 20 elements in 12 groups with no aspherical elements. The Z 70-200 has 21 elements in 18 groups including two aspherical elements and the TC-1.4x adds 6 elements, the TC-2.0x 8. [+]
Closest focus distance is 0.71m (2.3ft.) with a working distance of 0.47m (1.5ft.) at 100mm focal length. At 400mm focal length minimum focus distance is 0.97 (3.2ft.) which results in a working distance of 0.68m (2.3ft.) and a maximum magnification of 1:2.5 which is very good. Using teleconverters increases maximum magnification to 1:1.8 with the TC-1.4x or 1:1.3 with the TC-2.0x without changing the working distance. The other lenses in this comparison also achieve their maximum magnification at their longest focal length: This is 1:4.1 at 1.3m working distance for the F-Nikkor. The Z 70-200 achieves 1:4.6 at 0.72m working distance. Use it with a teleconverter and maximum magnification increases to 1:3.3 or 1:2.3. The Z 100-400 achieves a magnification of 1:10 at 3.98m object distance (and 400mm focal length). [+]
Image stabilization: All three Nikkors offer optical stabilization (VR) which works in conjunction with the body-based stabilization on Nikon’s full-frame Z cameras to achieve a claimed 5.5 stops of stabilization over 5 axes for the Z 100-400 and Z 70-200. For the F-Nikkor the Z bodies only add roll correction to pitch and yaw correction from the lens’s VR. [+]
Filter-thread: All three lenses in this comparison use 77mm filters. [+]
Autofocus: Yes with built-in AF drive. Manual-focus override is by simply turning the dedicated focus ring at the middle of the lens. The focus ring cannot be re-assigned another function nor can it be switched off. The focus ring has a variable gearing (like all AF Z-Nikkors so far) which allows for very precise manual focus when turned slowly but cannot be switched to linear gearing. Which makes smooth focus pulling for videographers almost impossible. On Nikon Z cameras introduced October 2020 or later you can reverse focus direction. Focus on the F-Nikkor works differently as it has a direct linear mechanical coupling between the focus ring and the focus action. [+]
Display: The Nikon Z 100-400mm f4.5-5.6 VR S features the same OLED display as the Z 70-200 indicating focal length, aperture, or focusing distance (in m or ft.) and depth-of-field. This display is hard to read under sunny conditions in its default setting but it can be made as bright as the top display on the Z7. You can switch through the different display types using the DISP-button. The F-Nikkor has no such display but sports the usual distance and dof indicators on the focus ring. [+]

Additional functions: There are 4 function buttons directly behind the zoom ring one of them designated L-Fn2 plus an additional L-Fn button behind the focus ring on the lens which can be assigned different functions like AE/AF lock. That is the same as with the Z 70-200. The F-Nikkor has no such function buttons. All three lenses also sport a focus-limiter which in case of the Z 100-400 prevents the lens to search focus closer than 3m (10ft.). Interestingly the Z 100-400 does not sport a zoom lock and the marketing material claims the lens does not show zoom creep. [+]
Aperture: The lens has a slim multi-function control ring just in front of the tripod collar in addition to the dedicated focus ring. The control ring can be assigned to operate the aperture (which is the default), exposure compensation, or ISO sensitivity – or simply switched off. Position and texture of the ring on the Z 100-400 has changed over previous models like the Z 70-200: It moved quite a bit forward from the narrow throat of the lens mount to the wider part of the barrel which makes it easier to reach when you hold the lens. The Z 100-400 has a variable focal ratio starting at f4.5 on the wide end. It gets successively darker when you zoom in: f4.8 from 125mm, f5.0 from 185mm, f5,3 from 270mm, f5.6 from 380mm. This is a tad brighter than the F-Nikkor and also better than using the Z 70-200 with TC-2.0x which results in a constant f5.6 focal ratio. The F-Nikkor has no dedicated aperture ring. [+]
Lens profile: The Z-Nikkors come with a lens profile which can be controlled from the camera. Vignette control offers the usual options of High, Normal, Low and Off. Diffraction compensation and Auto distortion control can be activated or deactivated. The F-Nikkor has a lens profile in Adobe’s RAW converter. [+]
All three lenses cover full frame/FX or smaller sensors. [+]
Price: 2999 EUR (incl. 19% VAT) / 2700 USD / 2699 GBP. The Nikon AF-S 80-400mm f4.5-5.6G ED VR is 2030 EUR / 2300 USD / 2000 GBP, the Nikon Z 70-200mm f2.8 VR S costs 2330 EUR / 2600 USD / 2300 GBP. The price in EUR seems too high – especially compared to the price in USD. [0]
Use with teleconverters: Yes. Nikon offers two teleconverters for Z-mount: The TC-1.4x for 549 EUR (incl. 19% VAT) / 547 USD / 549 GBP and TC-2.0x for 660 EUR / 597 USD / 580 GBP. They can be used with the Z 100-400mm f4.5-5.6 VR S and Z 70-200mm f2.8 VR S – but no other Z-Nikkor so far. And you cannot use the Z teleconverters with the FTZ adapter. [+]
Both Z-Nikkors come with the usual flimsy pouch with no strings to pull it close. The lens hood is included and locks in place to avoid accidentally falling off plus it is reversible for transport. But while the lens hood of the Z 70-200 is coated like black velvet on the inside to reduce reflexes, the lens hood for the Z 100-400 has a stepped design. All three lenses have a detachable tripod foot – although the third-party replacements for the foot of the F-Nikkor will not work with the Z-Nikkors. But the good news is that you can swap the (replacement) foots between the Z 70-200 and Z 100-400. The F-Nikkor comes with a soft pouch and reversible lens hood. [0]
Sealing: yes. All three lenses have a rubber grommet at the lens-mount plus further special weather-sealing throughout the construction including towards the lens cap. [+]
At a score of 0[-]/4[0]/12[+] the Nikon Z 100-400mm f4.5-5.6 VR S offers a lot of useful features including optical image stabilization, full weather sealing and fluorine-coating, ARNEO plus Nano anti-reflex coating, the nifty OLED display and the multi function ring. Plus it works with teleconverters making the combo reach to 800mm focal length – albeit at a measly f11 focal ratio. Compared to the Nikon AF-S VR 80-400mm f4.5-5.6G ED VR the new lens is pretty much the same size but over 100g lighter – or around 250g lighter if you count the FTZ adapter in should you use the F-Nikkor on a Z body. This does not seem much but it certainly makes it easier to carry all day.
Coverage
With its 4x zoom the Nikon Z 100-400mm f4.5-5.6 VR S covers a slightly narrower range than the 5x zoom of the Nikon AF-S VR 80-400mm f4.5-5.6G ED VR. On the short end the F-Nikkor has an angle of view of 30.3 degrees, compared to 24.4 degrees of the Z-Nikkor. Using the Z 70-200mm f2.8 VR S with TC-2.0x covers a 2.9x zoom range starting with an angle of view of only 17.6 degrees.
Here is the angle of view of the different options (Auto distortion control activated):
Above: Nikon Z 100-400mm f4.5-5.6 VR S coverage on a full-frame camera at 100mm (left) and 400mm (right)
Above: Nikon AF-S VR 80-400mm f4.5-5.6G ED VR coverage on a full-frame camera at 80mm (left) and 400mm (right)
Above: 140-400mm coverage on a full-frame camera (simulated with Nikon Z 100-400mm f4.5-5.6 VR S)
Above: Nikon AF-S VR 80-400mm f4.5-5.6G ED VR + TC-1.4x coverage on a full-frame camera at 140mm (left) and 560mm (right)
The differences of starting at 80mm, 100mm, or 140mm are quite obvious and could be the decisive factor for choosing a long telephoto zoom lens.
Focus and zoom
Focus accuracy and repeatability is critical to consistently produce sharp shots. Repeatability (the accuracy of focus on the same subject after repeated focus-acquisition) of the Nikon Z 100-400mm f4.5-5.6 VR S is very good (measured 99.3% in Reikan FoCal) with no outliers over a series of 40 shots. The lens focuses in around 0.5 sec from infinity at 200mm focal length to 2.11m (1:10 magnification), which is fast.
The zoom ring has a pretty short throw of 80 degrees and has a 45mm wide rubber surface with a good grip. It turns with quite some resistance and cannot be operated with one finger. The lens shows no zoom creep and the center of gravity hardly shifts when the lens extends. This is quite a unique feature and Nikon explains it in this video. The focus ring is 17mm wide and is located closer to the camera. It also has a rubberized surface, moves smoothly, and can easily be operated even with your pinky.
Above from left to right: Nikon AF-S 80-400mm f4.5-5.6G ED VR on FTZ adapter, Z 100-400mm f4.5-5.6 VR S, Nikon Z 70-200mm f2.8 VR S on Z TC-1.4x
AF-operation of the lens in photo-mode can be heard as a low buzz from the outside but if you record video with the built-in microphone AF is silent – as is VR operation.
As you pull focus, you’ll notice practically no focus breathing: the image became 0.2% more magnified when I adjusted focus from infinity to 2.09m at 200mm focal length. This is not visible when shooting videos. Same at 100mm focal length.
I also tested whether Nikon’s zoom lens allows you to change the focal length without altering its focus. This characteristic is called parfocal. I focused the lens at 400mm and then slowly zoomed back checking focus on the way. The Z 100-400mm f4.5-5.6 VR S did keep its focus but not quite perfect: when zooming back the lens became gradually less sharp and then suddenly snapped back into perfect focus. See the following 100% crops shot at f5.6 and a focal length of 281mm and 280mm without re-focusing:

Image stabilization
To test the effectiveness of the image stabilization with the Nikon Z 100-400mm f4.5-5.6 VR S on a Nikon Z7 camera body, I did a series of 140 test-shots hand-held at 400mm focal length with shutter speeds from 1/400 of a second down to 1/12 sec. I used the shots at 1/400 sec with VR=off as reference of how good my hand-holding was at the time of the test and Reikan FoCal did the chore of evaluating the sharpness of all shots.
Here’s the results: With VR=on the combined stabilization from lens and camera produced only 4 outliers in the 80 shots down to 1/50 sec (3 stops) but the rest was clearly better than the average sharpness at 1/400 sec with VR=off. At 1/25 sec (4 stops) I had two outliers over 20 Shots and at 1/13 sec (5 stops) results were on average still very sharp, with only 3 outliers in 20 shots. This is a very impressive performance of the combined optical and sensor-based image stabilization supporting Nikon’s claim of 5.5 stops.
Above from left to right: Nikon AF-S 80-400mm f4.5-5.6G ED VR on FTZ adapter, Z 100-400mm f4.5-5.6 VR S, Nikon Z 70-200mm f2.8 VR S on Z TC-1.4x
Next check out my quality results!
Check prices on the Nikon Z 100-400mm f4.5-5.6 at B&H, Adorama, WEX UK or Calumet.de. Alternatively get yourself a copy of my In Camera book or treat me to a coffee! Thanks!
 Nikon's Z 100-400mm f4.5-5.6 VR S is a worthy successor to the venerable AF-S 80-400mm f4.5-5.6G ED VR which the new lens surpasses in almost every aspect. It produces very sharp images with almost no field-curvature or colour aberrations and can confidently be used wide open and with a 1.4x teleconverter. Its Bokeh is quite nice and the optical image stabilization of over 5 stops should prove helpful with the challenges of hand-holding a 400mm lens. It may lack the ability of its predecessor to zoom back to 80mm but all-in-all the Z 100-400mm f4.5-5.6 VR S certainly earns a Highly Recommended.
Nikon's Z 100-400mm f4.5-5.6 VR S is a worthy successor to the venerable AF-S 80-400mm f4.5-5.6G ED VR which the new lens surpasses in almost every aspect. It produces very sharp images with almost no field-curvature or colour aberrations and can confidently be used wide open and with a 1.4x teleconverter. Its Bokeh is quite nice and the optical image stabilization of over 5 stops should prove helpful with the challenges of hand-holding a 400mm lens. It may lack the ability of its predecessor to zoom back to 80mm but all-in-all the Z 100-400mm f4.5-5.6 VR S certainly earns a Highly Recommended.