Nikon 24-120mm f4G VR review
-
-
Written by Thomas
Intro
The Nikkor AF-S 24-120mm f/4.0G ED VR is a 5x zoom that’s compatible with full-frame Nikon FX bodies. Announced in August 2010 with its gold-ring, constant f4.0 aperture, and a price-tag of around 1000 EUR it defined a new kind of zoom-class for Nikon right between the affordable general-purpose zooms (like the newer Nikon AF-S 24-85mm f/3.5-4.5G VR) and the professional f2.8 zooms like the Nikon AF-S 24-70mm f/2.8G. It’s the successor to the Nikon 24-120mm f/3.5-5.6G IF-ED VR from 2003 and now sports improved Vibration Reduction and Nano Crystal Coating in addition to the constant f4.0 aperture.
While 24-120mm is an ideal general-purpose range for full-frame bodies, there’s no reason why you can’t use it on a DX body where it will deliver an equivalent of 36-180mm coverage and of course offer future-proofing should you upgrade to an FX body at a later date. Indeed the 24-120mm makes a lot of sense for DX bodies when complemented with, say, the DX 10-24mm, seamlessly covering a 12x range from ultra-wide-angle to decent tele-reach with only two lenses.
The AF-S 24-120mm f/4.0G VR is sort of the “middle child” in the current set of three stabilized FX general-purpose zooms starting at a decent wide angle and zooming in to various degrees of tele-coverage: there’s the latest 24-85mm, the 24-120mm I’m reviewing here and 28-300mm FX-superzoom. As the only lens of this trio with a gold-ring (and a price-tag to match) it will be interesting to see how the 24-120mm performs under the tough demands of a 36MP FX-sensor. So in this review I’ll scrutinize Nikon’s AF-S 24-120mm f/4.0G VR to see whether it is a good match for Nikon’s highest resolution DSLR.
 |
Facts from the catalog
As usual I’ll have a look at the technical data first. I’ve rated the features with a [+] (or [++]), when it’s better than average or even state of the art, a [0] if it’s standard or just average, and [-] if there’s a disadvantage.
 | |
Size (diam. x length): 84 x 104 mm (3.3 x 4.1 in.). Diameter grew by 7mm and length by 10mm over its predecessor, the AF-S 24-120/3.5-5.6G VR. Only 10mm shorter than the AF-S 28-300/3.5-5.6. [0]
Weight: 710 g (25 oz) = 135g heavier than its predecessor which did not offer a constant f4.0 aperture. Well balanced on an FX-body but you notice its weight on a lighter DX-body. [0]
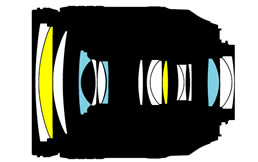
Optics: 17 elements in 13 groups. The older sibling has a 15/13 design. Flares and ghosts can result from too many air/glass-surfaces and Nikon has added Nano-coating to reduce this. We’ll see in my test how well this works. The cross-section shows three aspherical and two ED-glass elements. [+]
Closest focus distance/max. magnification: 0.45 m (1.5 ft.) / 1:4.2. In my test I was able to go down to 1:3.7. This is pretty useful in capturing flowers close-up. [+]
Filter-thread: 77mm = standard with most pro-lenses [+]
IS: Yes = helps a lot [+]
AF: AF-S with SWM (silent wave motor), so it will autofocus on D60/3×00/5×00-bodies, and there’s manual-focus override by simply turning the focus ring [+]
Covers full frame/FX or smaller = very good [+]
Price: around 1000 EUR new (incl. 19% VAT) = pretty hefty. Especially as its predecessor, the Nikon AF-S 24-120mm f/3.5-5.6G VR, can be had for as little as 600 EUR now. [-]
Comes with a flexible lens pouch, lens-shade is included and reversible for transport, and the lens-caps are standard Nikon’s. [0]
Distance information is relayed to the camera, so the Nikon body can do all the advanced exposure-related stuff with this lens. But this is true for most alternatives too. [+]
Aperture ring = no, just like all Nikon G-lenses. [0]
Sealing: yes! A rubber grommet at the lens-mount. [+]
So the score in the “features-department” is 1[-]/4[0]/8[+]. All-in-all the lens sports many good features. For prospective buyers the question boils down to whether they’ll be willing to pay a hefty premium for the constant f4.0 aperture and Nano-coating.
Motivation
:
A stabilized 5x zoom with a focal range of 24-120mm may be your to-go lens on an FX-body when you want to be prepared for many standard situations. At 24mm shortest focal length it lets you capture a crowd in tighter spaces or shoot landscapes and architecture. And the 120mm on the long end gives you enough reach and working distance for portraits and street-photography. Although it has a one stop smaller aperture than 24-70/2.8 zooms its image stabilization should compensate for 2-4 stops over a non-stabilized alternative. That gives you a 1-3 stop advantage of hand-holding power under dim or fading light. Be aware though that image-stabilization is no advantage for fast-moving subjects like children or sports. In the latter shooting situations you should crank-up the ISO to get faster shutter-times.
Alternatives
:
– The new Nikon AF-S 24-85/3.5-4.5G VR: Shorter, lighter, cheaper (at around 500 EUR currently). Not of constant aperture but close. A pretty good performer, see my Nikon Nikkor AF-S 24-85mm f/3.5-4.5G VR review.
– Then there are the 24-70/2.8 zooms from Nikon, Sigma and Tamron (the latter even offering image stabilization) with prices starting at 750 EUR and going up to 1500 EUR. All offer a larger aperture but are missing 50mm on the long end. That is a lot and you would have to crop 1.7x with a 70mm focal length to get the same angle of view as with a 120mm lens. That would reduce a full resolution image from a 36MP D800 to only 12MP!
– The other alternative is Nikon’s AF-S 28-300mm f/3.5-5.6G VR for around 850 EUR or the cheaper Tamron AF 28-300mm 3.5-6.3 XR Di VC. Both offer the broadest zoom-range at 11.7x giving you 2.5x more reach on the long end but starting only at 28mm. That may not be wide enough for your purposes.
 The Nikon 24-120/4.0G VR delivers good overall performance, but unfortunately the FX-corners look like the lens has been designed with only a 12MP FX-sensor in mind: On a 36MP full-frame sensor you need to stop down to f8 to lift FX-corner performance to good levels. That said, it is a worthy kit-zoom for any Nikon FX-body and its 5x zoom range with a useful minimum focus distance is very practical in many situations. Plus on a DX-body it mostly delivers good to very good performance, even reaching excellent levels in the center up to 70mm.
The Nikon 24-120/4.0G VR delivers good overall performance, but unfortunately the FX-corners look like the lens has been designed with only a 12MP FX-sensor in mind: On a 36MP full-frame sensor you need to stop down to f8 to lift FX-corner performance to good levels. That said, it is a worthy kit-zoom for any Nikon FX-body and its 5x zoom range with a useful minimum focus distance is very practical in many situations. Plus on a DX-body it mostly delivers good to very good performance, even reaching excellent levels in the center up to 70mm.



