Tamron 90mm f2.8 Di III Macro review
-
-
Written by Thomas
Quality
Testing: Longitudinal Chromatic Aberration and focus shift
Lenses with focal ratios of f2.8 or larger are often prone to longitudinal color aberrations (loCA, a.k.a. “axial color” or “bokeh CA”). These show up as magenta coloration in the foreground and greenish hues in the background and are not easily corrected in post-processing. The Tamron 90mm f2.8 Di III macro shows only a small amount of loCA at normal distances although more than the Nikon Z MC 105mm f2.8 VR S. Focus shift is not an issue.
The following images are 50% crops from 180MP images obtained from 16 image pixel shift shooting on a 45MP Nikon Z8. This has the advantage of eliminating color moiré which would otherwise distract from the coloration from loCA. You can click on the images to access the full resolution 100% crops.
Tamron 90mm f2.8 Di III macro loCA; 50% crop from 180MP image
Above from top to bottom: f2.8, f4.0, f5.6; left = foreground, right = background
The following shot shows that the Tamron 90mm f2.8 Di III macro produces no purple fringing around high-contrast edges or specular highlights in the focus plane. Spill-over of bright background light is hardly an issue as is green outlining around background subjects:
Above: Tamron 90mm f2.8 Di III macro at f2.8, 100% crop, 100% crop; click image for 4k version, here for large original
Sharpness and contrast
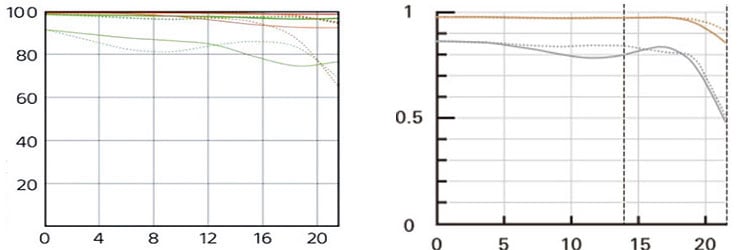
Let’s have a look at the theoretical performance of the Tamron 90mm f2.8 Di III Macro and compare it to some alternatives:
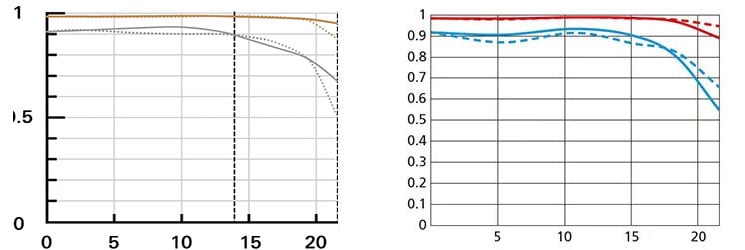
Above: Tamron 90mm f2.8 Di III Macro at f2.8 (left), Nikon Z MC 105mm f2.8 VR S at f2.8 (right)
Above: Sony FE 90mm f2.8 Macro G OSS at f2.8 (left), Tamron 90mm f2.8 Macro VC II at f2.8 (right)
These MTF charts show the computed lens-performance of lenses wide open at infinity without influence of diffraction at 10 line-pairs/mm (red) and 30 lp/mm (blue) except for the charts of the Sony where the red lines show the performance at f8.0. Higher values are better (more contrast) and the closer the dotted and solid lines are together the less contrast dependents on the orientation of the test-pattern (less astigmatism). The x-axis displays the distance from the optical axis (=center of the sensor) in mm.
From the charts the Tamron 90mm f2.8 Di III Macro looks on a par with Nikon’s Z MC 105mm f2.8 VR S and sharper than the Sony FE 90mm f2.8 Macro G OSS and its predecessor, the Tamron 90mm f2.8 Macro VC II. But remember: The MTF charts show contrast and resolution at infinity. Performance of these lenses in close-up shooting up to 1:1 magnification may produce different results.
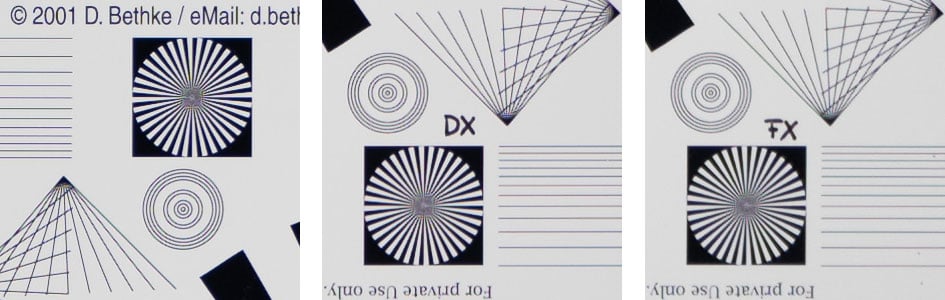
Let’s see how this theoretical performance translates into real life results in the sharpness test based on Siemens-stars shot on a 45MP Nikon Z8 set to 16 image Pixel shift shooting. The 16 individual images for each shot were merged in NX Studio 1.7.0 into a 180MP RAW file and further processed in Lightroom 14.0/CRAW 17.0 to Adobe Color profile with the lens profile compensating CA, distortions and vignetting. Noise-reduction was set to 0, sharpening to 50/1/36/10, with no extra tone, color, or saturation adjustment. White-balance was adjusted to a neutral white and I did some exposure compensation to make the brightness of all crops match. So you will not see light fall-off in the corners. I also focused separately for the center, the DX-corner, and FX-corner which eliminates any effect field-curvature might have. If you want to know more about the advantages and perils of pixel shift shooting head over to page 2 of my Tamron 28-75mm f2.8 Nikon Z review.
The following 50% crops from 4 mm, 13 mm, and 20 mm image height show the Tamron 90mm f2.8 Di III Macro from f2.8 down to f11. For comparison I use 100% crops from the Nikon Z MC 105mm f2.8 VR S shot on a 45MP Nikon Z7 and Sony FE 90mm f2.8 Macro G OSS shot on a 42MP Sony A7R II (no pixel shift shooting). This comparison may not be apples-to-apples but is close enough to draw some conclusions.
Tamron 90mm f2.8 Di III Macro compared; 50% crop from 180MP image
Above: Tamron 90mm f2.8 Di III Macro at f2.8; click image for full resolution 100% crops
Above: Nikon Z MC 105mm f2.8 VR S at f2.8; also available at f4.0, f5.6, f8.0, f11

Above: Sony FE 90mm f2.8 Macro G OSS shot on a Sony A7R II at f2.8; also available at f4.0, f5.6, f8.0, f11
Above: Tamron 90mm f2.8 Di III Macro at f4.0; click image for full resolution 100% crops
Above: Tamron 90mm f2.8 Di III Macro; click image for full resolution 100% crops; also available at f8.0, f11
Summary:
Wide open, the Tamron is very sharp within the DX/APS-C image-circle and only a bit softer towards the FX/FF-corner. Both the Nikon Z MC 105mm f2.8 VR S and the Sony FE 90mm f2.8 Macro G OSS look pretty similar to the Tamron with a slightly sharper FX-corner. At the testing distance of 4m field-curvature of the Tamron 90mm f2.8 Di III macro is pretty low.
Performance at long distances
The Siemens-star test-targets are shot at a distance of 45x focal length (i.e. at around 4m). But performance of lenses also depends on the shooting distance. Therefore, I shot another series of a city around 1 km away. Processing was done in Lightroom 14.0/CRAW 17.0 from RAW to Adobe Color profile with the lens profile compensating CA, distortions and vignetting. Noise-reduction was set to 0, sharpening to 50/0.5/36/10, with no extra tone, color, or saturation adjustment. I used manual focus at the largest aperture and did not change focus for other apertures. All shots were made from a heavy tripod with image stabilization switched off at ISO 64. As usual I have selected the diagonal that provided the better corner results as the lens was slightly decentered.
The following images show the complete scene wide open plus 100% crops from near center, DX/APS-C-corner, and FX/FF-corner. All crops in a row are from the same image so there is no compensation for field curvature. You can access the large originals, but the files are for personal evaluation only and cannot be used in another publication or website without permission.
Above: Tamron 90mm f2.8 Di III Macro at f2.8; click image for 4k version, here for large original

Above: Tamron 90mm f2.8 Di III Macro at f2.8

Above: Tamron 90mm f2.8 Di III Macro at f4.0

Above: Tamron 90mm f2.8 Di III Macro at f5.6; also available at f8.0
Summary:
At long distances the results from the previous test are confirmed: The Tamron 90mm f2.8 Di III macro shows very high resolution up to the DX/APS-C corners even wide open. Only the FX/FF-corner profits a bit from stopping down.
Vignetting and distortions
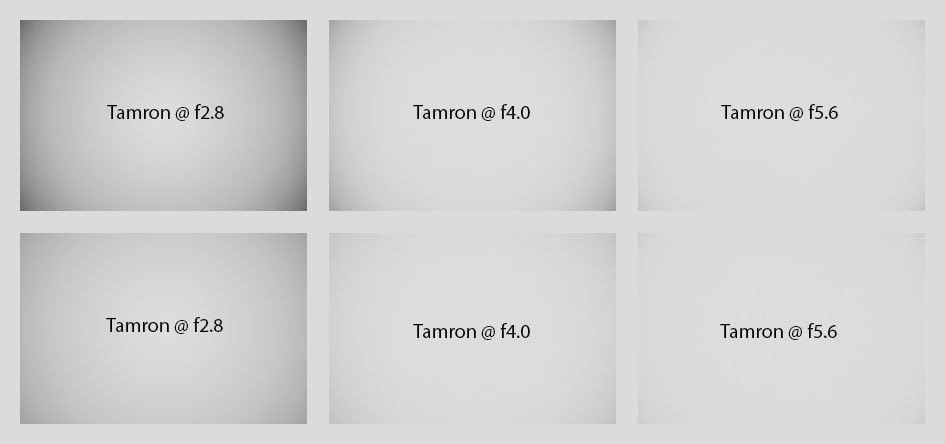
To make it easier to see light fall-off in the corners of a full-frame sensor I’ve arranged a series of three shots each with the Tamron 90mm f2.8 Di III macro. Processing was done in Lightroom 14.0/CRAW 17.0 from RAW to Adobe Color profile with the lens profile compensating CA, vignetting (as set in camera), and distortions and developed to the same brightness in the center. They are shown with vignette control Off (1st row) resp. Normal (2nd row).
Above: Tamron 90mm f2.8 Di III macro
Wide open vignetting is pretty mild with the lens profile applied. And from f4.0 onward vignetting is a non-issue. And this is at infinity. At close-up shooting vignetting is even lower. With vignette control set to Normal the extreme corners are lifted by about 0.8 EV at f2.8.
Handling of lens profiles by Adobe’s RAW converter continues to be confusing: The Tamron 90mm f2.8 Di III macro gets its lens profile applied as it was set in camera but you can change this in post-processing with sliders to control the strength of vignetting and distortion correction between 0 and 200%: Very good! But if you set either correction in camera to Off the slider to control the strength of vignetting and/or distortion in Lightroom or CRAW is disabled (NX Studio can switch corrections back on). So it’s better to leave the lens profile in camera On which enables all options when processing the image in Lightroom/CRAW.
The following composite image shows the upper half of a large screen TV set displaying grid lines for the full frame and cropped frame. Distortions are slightly barrel and are perfectly corrected for by the lens profile:

Distortions: Tamron 90mm f2.8 Di III macro, as is (top) / with lens-profile (bottom)
Rendering of point-light sources at night-shots
Night-shots pose a different challenge for lenses as the contrast is even higher than under bright sun and point-light sources can reveal some weaknesses such as coma, haloing and colour-aberrations that do not show up as prominently in other test-shots. The 100% crops below the main image show the effect of coma in the FX-corner of the Tamron 90mm f2.8 Di III macro at different apertures:
Above: Tamron 90mm f2.8 Di III macro at f2.8; click image for 4k version, here for large original

Above: Tamron 90mm f2.8 Di III macro; 100% crops from the FX/APS-C-corner at f2.8, f4.0, f5.6
The Tamron 90mm f2.8 Di III macro shows no visible coma. The test also showed neither coloration nor halos around bright streetlights.
Bokeh quality
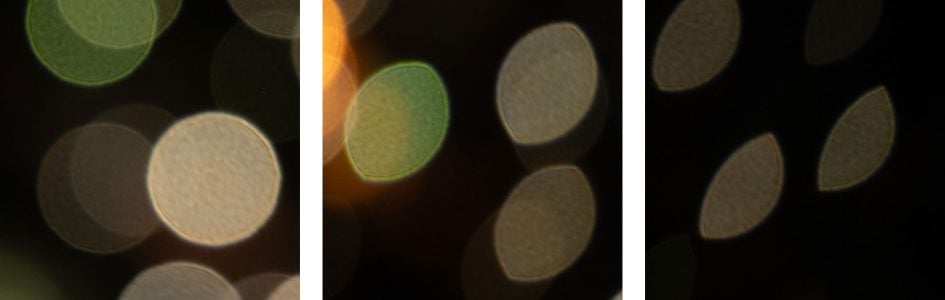
This test is for the rendering of point-light sources in an out-of-focus background. The circle of confusion that is produced by the test is pretty indicative of Bokeh performance (in the background) and light fall-off. Ideally the out-of-focus image of the point-light is evenly lit and perfectly circular, with no “onion-rings”, and without coloration. Large aperture lenses normally produce an effect known as “cat’s eye” the further away from the optical axis the point-light is projected. This is due to optical vignetting in the lens barrel when light enters the lens from an angle.
Above: Tamron 90mm f2.8 Di III macro at f2,8; click image for 4k version
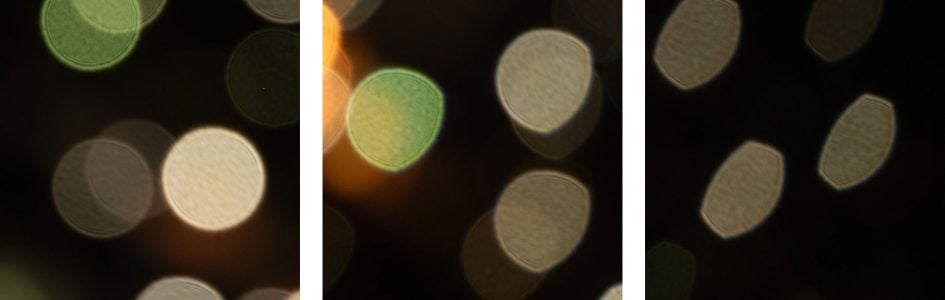
Above: Tamron 90mm f2.8 Di III macro at f3.0; click image for 100% crops
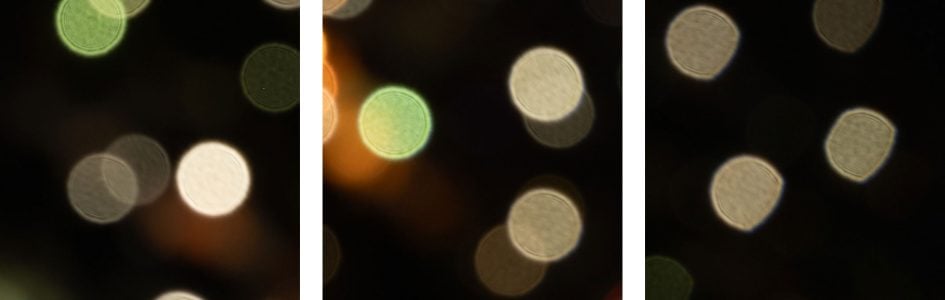
Above: Tamron 90mm f2.8 Di III macro at f4.0; click image for 100% crops
Above: Tamron 90mm f2.8 Di III macro at f5.6; click image for 100% crops
Above: Tamron 90mm f2.8 Di III macro at f8.0; click image for 100% crops
The diameter of the Bokeh balls in the center is determined by the entrance pupil of the lens which is 32mm. Compression of the circle towards the corners is pretty strong wide open and still persists at f5.6. The inside of the Bokeh balls is slightly textured but without onion-rings. Outlining is minimal and there’s no coloration from loCA.
Let’s see how this analysis of out-of-focus point-light sources translates into Bokeh-performance shooting a book-shelf. Crops are from the foreground, middle-ground, and background resized to make them comparable across all my reviews. Crops are from wide open compared to the Nikon Z MC 105mm f2.8 VR S and the Sony FE 90mm f2.8 Macro G OSS.
Above: Tamron 90mm f2.8 Di III macro at f3.0; click image for 4k version, here for large original
Above: Tamron 90mm f2.8 Di III macro at f3.0; click image for 100% crops, here for large original
Above: Nikon Z MC 105mm f2.8 VR S at f2.8; click image for 100% crops, here for large original
Above: Sony FE 90mm f2.8 Macro G OSS at f2.8; click image for 100% crops, here for large original
Bokeh from the three lenses looks almost indistinguishable and is actually pretty nice for very sharp lenses with a focal ratio of f2.8. Looking closely the Tamron renders the foreground slightly softer than the Nikon. In the transition zone the Sony seems to have the advantage but this may be due to a slightly closer focus.
Looking at the ruler (below, now at 100%) shows that the Tamron 90mm f2.8 Di III macro produces some artifacts (above “57”) and a bit of double-contours. The Nikon seems a bit better in this respect, while the Sony looks the smoothest of the three. But again: differences are pretty small.

Above: Tamron 90mm f2.8 Di III macro at f3.0; 100% crop

Above: Nikon Z MC 105mm f2.8 VR S at f2.8; 100% crop

Above: Sony FE 90mm f2.8 Macro G OSS at f2.8; 100% crop
Find more examples to judge Bokeh of the Tamron 90mm f2.8 Di III macro on the next page.
Close-up performance
The Tamron 90mm f2.8 Di III macro achieves a maximum magnification of 1:1 in close-up shooting. The following crops are at 1:3.6 from 0mm, 13mm, and 19mm off the center of the sensor respectively. The area of sharp focus is 86 x 130mm. All crops in a row are from the same shot (with no focus adjustment).
Tamron 90mm f2.8 Di III macro, 1:3.6 magnification; 100% crops

Above: Tamron 90mm f2.8 Di III Macro at f3.5

Above: Tamron 90mm f2.8 Di III Macro at f5.6

Above: Tamron 90mm f2.8 Di III Macro at f11
The Tamron is very sharp within the DX/APS-C image-circle even wide open. Only the FX/FF-corner is a bit softer and profits from stopping down to f5.6 where the lens is so sharp that you can clearly see the loss in contrast from diffraction when stopping further down to f11. There’s also no discernible field curvature. Very good!
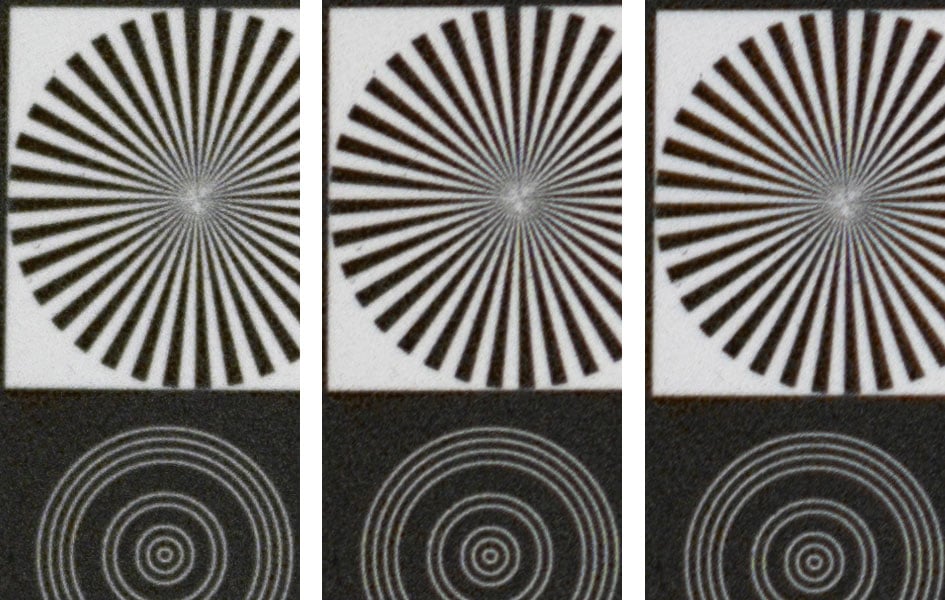
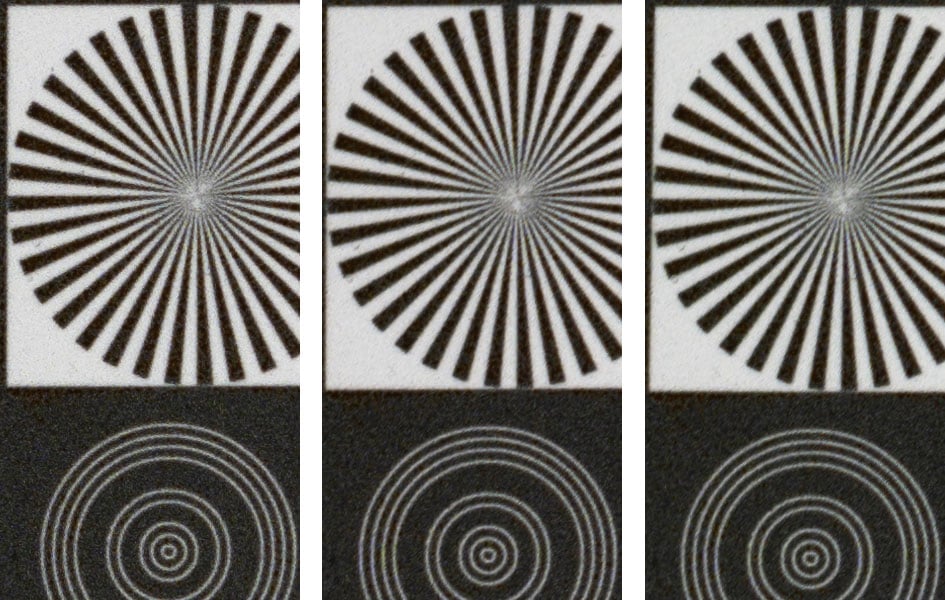
The next set of images was shot from a low ISO b&w film negativ at 1:1 magnification. So the “noise” that you see in the crops is actually the film grain. The crops shown below are from 0mm, 14mm, and 19mm off the center of the sensor respectively. The lens was focused specifically for each crop which eliminates the risk of a misaligned target or any residues of field curvature. So this is the best result you can get from focus stacking multiple shots with the Tamron lens. Btw.: The target is identical in each crop, so any differences you see between crops in a row result from the different image heights at which they were shot.
Tamron 90mm f2.8 Di III Macro, 1:1 magnification; 100% crops
Above: Tamron 90mm f2.8 Di III Macro at f5.6
Above: Tamron 90mm f2.8 Di III Macro at f8.0
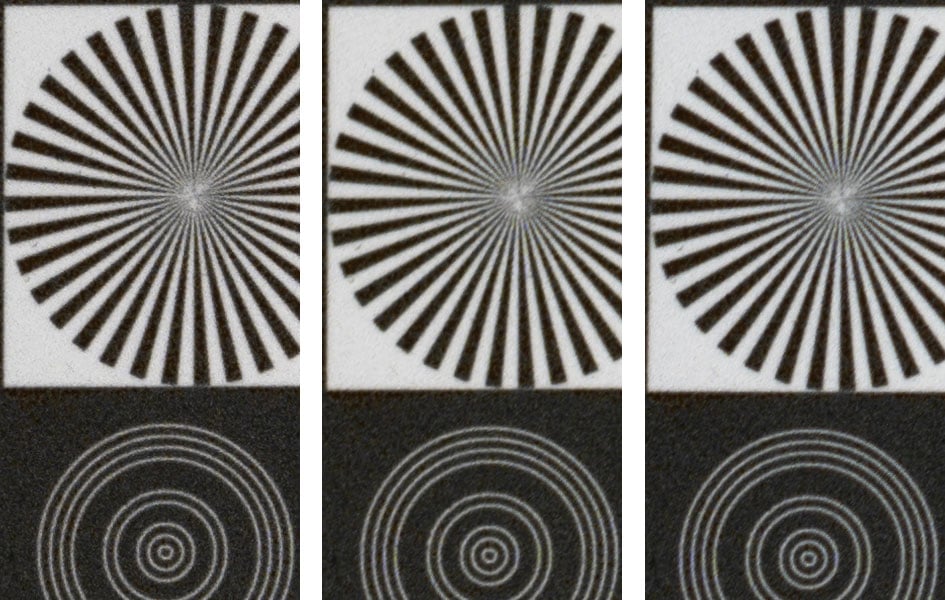
Above: Tamron 90mm f2.8 Di III Macro at f11
At f5.6 the Tamron 90mm f2.8 Di III Macro produces excellent sharpness in the center, very good results in the DX/APS-C-corner, and good sharpness in the FX-corner. Stopping down brings the FX/FF-corner closer to the DX/APS-C-corner but both areas do not reach the resolving power at the center.
Flare, ghosting, and sunstars
Catching a strong light-source shining directly into the lens is always a risky business: it could produce strange colorful ghost-images or reduce contrast considerably through flare and glare. The appearance of flare and ghosting depends on factors like the aperture and the angle of the light hitting the lens. To judge the proclivity of Tamron’s 90mm f2.8 Di III Macro for these artifacts I went through a series of well calculated shots at f11 and f2.8 against a strong light source to provoke glare and ghosting. The lens hood was mounted in all shots. Following is one of the more extreme example results. The little bright square inset in the upper left shows the respective area with an exposure compensation of +3 EV to make it easier to see which levels of black the lens renders at that point:
Above: Flare and ghosting. Strong light hitting the Tamron 90mm f2.8 Di III Macro at f11; click image for 4k version or here for +3 EV exposure compensation
The Tamron 90mm f2.8 Di III Macro has flares and ghosting relatively well controlled and produces a deep level of black outside these artifacts.
Sunstars start to develop at f5.6 but get better when the lens is stopped down to f8.0 (or f11, see above):

Above from left to right: Sunstars from the Tamron 90mm f2.8 Di III Macro at f4.0, f5.6, f8.0, 100% crops
Next check out my sample images!
Check prices on the Tamron 90mm f2.8 Di III Macro VXD at B&H, Adorama, WEX UK or Calumet.de. Alternatively get yourself a copy of my In Camera book, an official Cameralabs T-shirt or mug, or treat me to a coffee! Thanks!