Canon SX70 HS review
-
-
Written by Ken McMahon
Quality
To test real-life performance, I shot this scene with the Canon PowerShot SX70 HS and the Nikon COOLPIX B600 using their best quality JPEG mode. Both cameras were mounted on a tripod and image stabilisation was disabled. Program auto mode was selected for the exposure. For this first test I set the COOLPIX B600 to its 21mm equivalent maximum wide angle setting and nudged the zoom on the PowerShot SX70 HS in just a touch to match the slightly narrower field of view.

At its base 100 ISO sensitivity setting The PowerShot SX70 HS selected 1/1000 at f5. The COOLPIX B600 was set to its base 125 ISO sensitivity setting and it selected an exposure of 1/1250 at f3.8. As usual, the crops below are taken from the areas marked in red above.
The first thing to note is that the 20 Megapixel sensor in the PowerShot SX70 HS produces a smaller crop area with larger detail than the 16 Megapixel sensor in the COOLPIX B600. The second thing I noticed is the colour fringing on the first crop from the COOLPIX B600. Aside from that, there’s really not a great deal to separate these two sets of crops at the wide angle setting. The first and last edge of the frame crops from the Coolpix B600 look a tiny bit more detailed than those from the SX70 HS, and with cops two and three from the middle of the frame it’s the other way around. but the differences are very marginal and you’d only ever notice pixel-peeping these 100 percent crops.
Now scroll down to see how these two super-zooms compare when zoomed in to a middling focal length.

Above left: Canon PowerShot SX70 HS at 4.4mm f5 100 ISO. Above right: Nikon COOLPIX B600 at 4.3mm f3.8 125 ISO.

Above left: Canon PowerShot SX70 HS at 4.4mm f5 100 ISO. Above right: Nikon COOLPIX B600 at 4.3mm f3.8 125 ISO.

Above left: Canon PowerShot SX70 HS at 4.4mm f5 100 ISO. Above right: Nikon COOLPIX B600 at 4.3mm f3.8 125 ISO.

Above left: Canon PowerShot SX70 HS at 4.4mm f5 100 ISO. Above right: Nikon COOLPIX B600 at 4.3mm f3.8 125 ISO.
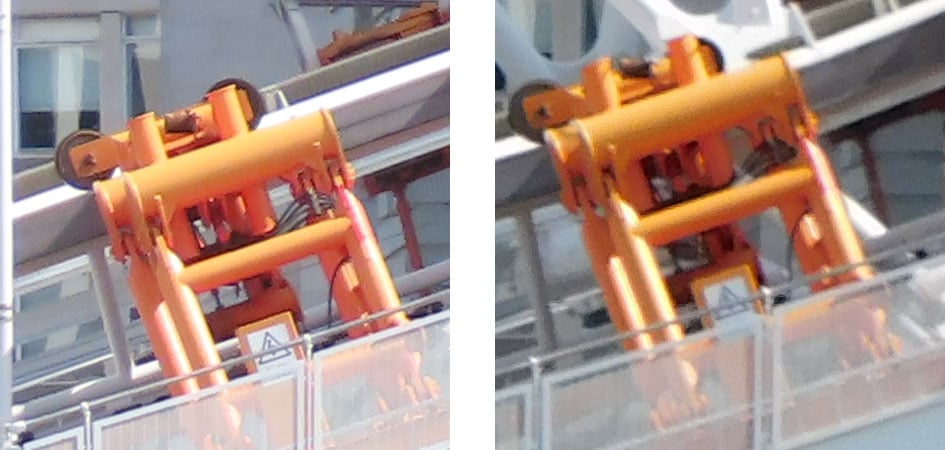
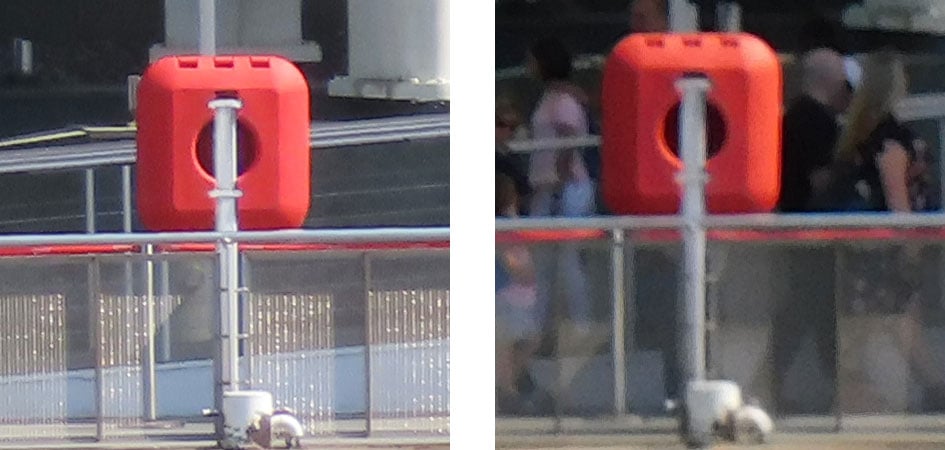
Canon PowerShot SX70 HS quality at 300mm equivalent

Here we’ve got three crops (1,3 and 4) from close to the frame edge and one (2) from nearer the middle. In every case, the crops from the CanonPowerShot SX70 HS look cleaner and more detailed. There’s a slight clumpiness to the detail in the Nikon COOLPIX B600 crops. Scroll down to see how they compare when the PowerShot SX70 HS is fully zoomed in to its 1365mm equivalent focal length.

Above left: Canon PowerShot SX70 HS at 45mm f5.6 100 ISO. Above right: Nikon COOLPIX B600 at 54mm f5.5 125 ISO.

Above left: Canon PowerShot SX70 HS at 45mm f5.6 100 ISO. Above right: Nikon COOLPIX B600 at 54mm f5.5 125 ISO.
Above left: Canon PowerShot SX70 HS at 45mm f5.6 100 ISO. Above right: Nikon COOLPIX B600 at 54mm f5.5 125 ISO.
Above left: Canon PowerShot SX70 HS at 45mm f5.6 100 ISO. Above right: Nikon COOLPIX B600 at 54mm f5.5 125 ISO.
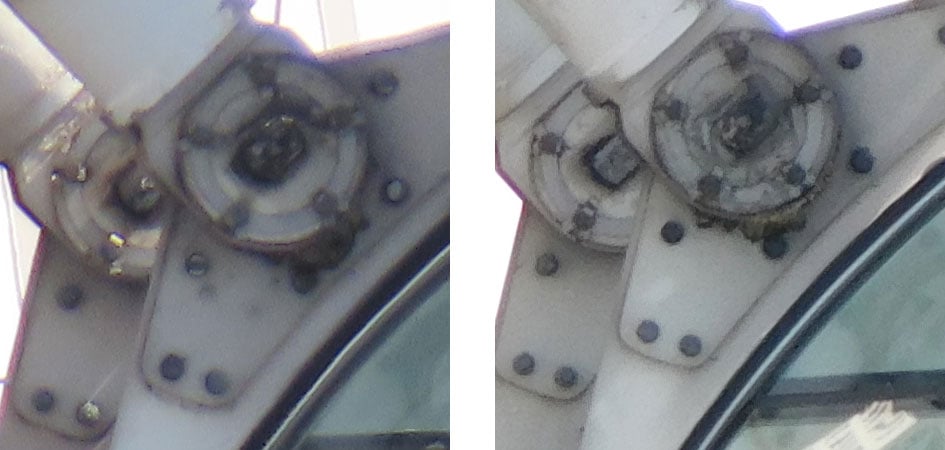
Canon PowerShot SX70 HS quality at 1440mm equivalent

Here I’ve zoomed both cameras in to their maximum telephoto focal length – 1365mm for the PowerShot SX70 HS and 1440mm for the COOLPIX B600. We can see some colour fringing on the first crop from the top left hand corner of the frame, but it’s far more prevalent in the PowerShot SX70 HS crop. And if you cast your eye down the remaining crops you’ll notice that while the B600 suffers from a bit of colour fringing here and there, it’s much more noticeable in the PowerShot SX70 Hs crops. I also think that at this focal length the B600 has the edge in terms of clarity and detail.
So overall a bit of a mixed bag with the PowerShot SX70 HS performing better at some focal lengths and the COOLPIX B600 at others, but no overall clear winner in terms of quality.
Now scroll down to see how these two models compare for noise performance.

Above left: Canon PowerShot SX70 HS at 1365mm f6.5 100 ISO. Above right: Nikon COOLPIX B600 at 258mm f6.5 125 ISO.

Above left: Canon PowerShot SX70 HS at 1365mm f6.5 100 ISO. Above right: Nikon COOLPIX B600 at 258mm f6.5 125 ISO.
Above left: Canon PowerShot SX70 HS at 1365mm f6.5 100 ISO. Above right: Nikon COOLPIX B600 at 258mm f6.5 125 ISO.

Above left: Canon PowerShot SX70 HS at 1365mm f6.5 100 ISO. Above right: Nikon COOLPIX B600 at 258mm f6.5 125 ISO.
Canon PowerShot SX70 HS JPEG Noise

To examine noise levels under real-life conditions, I shot this scene with the Canon PowerShot SX70 HS and the Nikon COOLPIX B600 at each of their ISO sensitivities using their highest quality JPEG settings. Both cameras were mounted on a tripod and stabilisation was disabled.
I set the COOLPIX B600 to its 24mm wide angle setting and zoomed the PowerShot SX70 HS in a tad to match the angle of view. Both cameras were set to Program auto mode; the PowerShot SX70 HS selected an exposure of 1/10 at f3.5 at it’s base 100 ISO sensitivity and the COOLPIX B600 selected 1/8 at f3.3 at its base 125 ISO setting. As usual the crops below are from the areas marked in red above. As with the quality crops above, the 20 Megapixel sensor in the PowerShot SX70 HS produces a smaller crop area with larger detail than the 16 Megapixel sensor in the COOLPIX B600.
This is an interesting, though perhaps not entirely unexpected set of results. Right from the off the Nikon COOLPIX B600 crop at 125 ISO looks a little cleaner and more detailed than the 100 ISO crop from the Canon PowerShot SX70 HS alongside it. And while there’s barely any change in the noise levels from 125 to 200 ISO in the COOLPIX B600, there’s a noticeable loss of detail in the SX70 HS.
At each step up the ISO sensitivity scale The SX70 HS loses out to the COOLPIX B600 with greater loss of image detail as a result of noise suppression. I’d say the 800 ISO B600 crop looks significantly better than the 400 ISO crop from the SX70 HS.
So if you’re looking for a super-zoom that’ll perform well in low light at higher ISO sensitivities, the COOLPIX B600 is the clear winner here.

Above left: Canon PowerShot SX70 HS at 100 ISO f3.5. Above right: Nikon COOLPIX B600 at 125 ISO f3.3.

Above left: Canon PowerShot SX70 HS at 200 ISO f3.5. Above right: Nikon COOLPIX B600 at 200 ISO f3.3.

Above left: Canon PowerShot SX70 HS at 400 ISO f3.5. Above right: Nikon COOLPIX B600 at 400 ISO f3.3.

Above left: Canon PowerShot SX70 HS at 800 ISO f3.5. Above right: Nikon COOLPIX B600 at 800 ISO f3.3.

Above left: Canon PowerShot SX70 HS at 1600 ISO f3.5. Above right: Nikon COOLPIX B600 at 1600 ISO f3.3.

Above left: Canon PowerShot SX70 HS at 3200 ISO f3.5. Above right: Nikon COOLPIX B600 at 3200 ISO f3.3.

Above Right: Nikon COOLPIX B600 at 6400 ISO f3.3.
Check prices on the Canon SX70 HS at B&H, Amazon, Adorama, or Wex. Alternatively get yourself a copy of my In Camera book or treat me to a coffee! Thanks!




